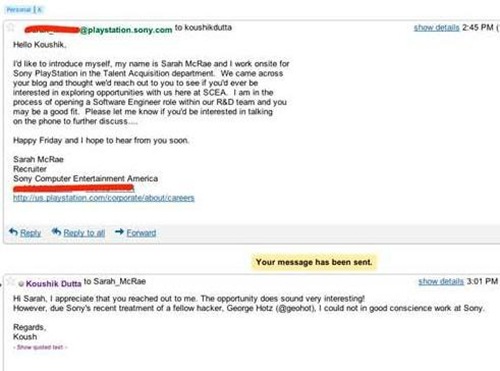
$127 Million USD Offensive Cyber Capabilities: 4.1 (1 = Low, 3 = Moderate and 5 = Significant)
Close ties with Russian Business Network (RBN), who is thought to own and operate the second
largest BotNet in the world. Intelligence suggests there are organized groups of hackers tied to the Federal Security Bureau (FSB).
The FSB is the internal counter intelligence agency of the Russian Federation and successor to the Soviet KGB. Russia is often overlooked as a significant player in the global software industry. Russia produces 200,000 scientific and technology graduates each year. This is as many as India, which has five times the population. This is hard to believe since their software industry can be traced back to the 1950s.
A study by the World Bank stated that more than one million people are involved in software
research and development. Russia has the potential to become one of the largest IT markets in
Europe. The Russian hacker attack on Estonia in 2007 rang the alarm bell. Nations around the world can no longer ignore the advanced threat that Russia’s cyber warfare capabilities have today and the ones they aspire to have in the near future.
From this information, one can only conclude that Russia has advanced capabilities and the intent and technological capabilities necessary to carry out a cyber attack anywhere in the world at any time.
USA Cyber Command

Web Site: http://www.stratcom.mil/factsheets/Cyber_Command
Estimated Personel: 5000
Description: Founded in 2010. United States Cyber Command (USCYBERCOM) is an armed forces sub-unified command subordinate to United States Strategic Command. The command is located in Fort Meade, Maryland and led by General Keith B. Alexander. USCYBERCOM centralizes command of cyberspace operations, organizes existing cyber resources and synchronizes defense of U.S. military networks.
USCYBERCOM plans, coordinates, integrates, synchronizes and conducts activities to: direct the
operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full spectrum military cyberspace operations in order to enable actions in all domains, ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries.
Relationship Designation: Neutral
Notes: The text „9ec4c12949a4f31474f299058ce2b22a“, which is located in the command’s emblem - is the MD5 hash of their mission statement. The command is charged with pulling together existing cyberspace resources, creating synergy and synchronizing war-fighting effects to defend the information security environment. USCYBERCOM is tasked with centralizing command of cyberspace operations, strengthening DoD cyberspace capabilities, and integrating and bolstering DoD’s cyber expertise.
Some military leaders claim that the existing cultures of the Army, Navy and Air Force are
fundamentally incompatible with that of cyber warfare, and have suggested a fourth branch of the military, a cyber-warfare branch. LTC Gregory Conti and COL John „Buck“ Surdu (chief of staff of the United States Army Research, Development and Engineering Command) stated that the three major services are „properly positioned to fight kinetic wars, and they value skills such as marksmanship, physical strength, the ability to leap out of airplanes and lead combat units under enemy fire. „Unfortunately,“ the two officers write, „these skills are irrelevant in cyber warfare. Technical expertise isn’t highly valued in the three services. Just look at military uniforms: no decorations or badges honoring technical expertise“, the officers point out. These officers suggest that „Ultimately, the role of fighting and winning in cyberspace is a military mission, which demands a military organization – one that can recruit, train and retain highly qualified cyber-warfare combatants.“
LulzSec

Web Site: http://twitter.com/#!/LulzSec
Estimated Membership: 500
Description: Founded in 2011. This group splintered off from Anonymous in spring 2011 in order to form a group which concentrated less on geo-politics and more on taking on adversaries that were a little more humorous.
Relationship Designation: Neutral
Notes: This group I still finding it’s way, but has already launched some impressive and well
publicized attacks. Some of the leaked data stolen in these attacks can be found here
http://thepiratebay.org/user/LulzSec/
Cult of the Dead Cow

Web Site: http://www.cultdeadcow.com
Estimated Membership: 500
Description: Founded in 1984. Based in Lubbock, Texas, CULT OF THE DEAD COW (cDc) is one of the most accomplished and oldest hacker groups in the computer underground. Widely considered (by themselves) to be the most elite people to ever walk the face of the earth, this think tank has been referred to as both „a bunch of sickos“ (Geraldo Rivera) and „the sexiest group of computer hackers there ever was“ (Jane Pratt, _Sassy_ and _Jane_ magazines). The cDc is a leading developer of Internet privacy and security tools, which are all free to the public. In addition, the cDc created the first electronic publication, which is still going strong.
Relationship Designation: Ally
Notes: The cDc Grand Imperial Dynasty includes a former Presidential Advisor on computer security, a Harvard researcher, a former U.N. official, an assistant district attorney, a professor of logic, an award-winning filmmaker, several published authors, a video game developer, an Eagle Scout, programmers of every sort, graphic artists, musicians, currency traders, and a Merovingian. And these are just the members who have chosen to make their association with the cDc known to the public.
For over twenty years, the cDc has proven itself as an innovative force in the computer
underground. In 1984, the cDc invented the electronic publication. In 1990, the cDc’s HoHoCon
defined the modern computer underground convention. In every U.S. Presidential Election since
1992, the cDc has run a candidate. In 1994, the cDc became the first computer undergound group to have its own Usenet newsgroup. In 1996, the cDc coined the term „hacktivism.“ Also in 1996, the Ninja Strike Force (cDc’s elite cadre of cheerleader-assassins) was founded. In 1997, years before everyone and their dog had jumped on the file sharing bandwagon, it was distributing original mp3-format music on its website. In 1998 and 1999, the cDc’s „Back Orifice“ series was launched to open the eyes of consumers regarding the security of their computer operating systems. To this day, Back Orifice and BO2k are among the most popular remote system administration tools among both hackers and IT professionals. Since 1999, Hacktivismo (a special projects group within the cDc) has been at the forefront of the ongoing struggle for human rights in and out of cyberspace. In 2002, the cDc and Hacktivismo drafted their own human rights-friendly software license and earned further distinction as the only underground computer groups to ever receive U.S. Department of Commerce approval to export strong encryption in software. In 2004, the cDc and the NSF launched the Bovine Dawn Dojo Forum, the greatest on-line community of all time.
Crewl Underground Madness

Web Site: http://www.blackhat.be
Estimated Membership: 500
Description: Founded in 1996. With four fulltime founding leaders and hundreds of supporting
members, Crewl Underground Madness (cum) is a belgian blackhat group specialized in network in security, hacking, coding and phreaking.
Relationship Designation: Potential Ally
Notes: This group has been quiet lately, although they have gotten some press for some impressive work they did helping people in Africa. Generally this is a small and dedicated group of very highly skilled hackers and their supporters. We have reached out to this group several times over the years but have received no response. I still feel however that they would make excellent allies.
Chaos Computer Club

Web Site: http://www.CCC.de
Estimated Membership: 10,000
Description: Founded in 1981. Chaos Computer Club is the oldest and largest hacker group in the world. The CCC describes itself as „a galactic community of life forms, independent of age, sex, race or societal orientation, which strives across borders for freedom of information….“ In general, the CCC advocates more transparency in government, freedom of information, and human right to communication. Supporting the principles of the hacker ethic, the club also fights for free access to computers and technological infrastructure for everybody.
Relationship Designation: Ally
Notes: The CCC hosts the annual Chaos Communication Congress, Europe’s biggest hacker congress, with up to 4,500 participants. Every four years, the Chaos Communication Camp is the outdoor alternative for hackers worldwide. The CCC started a new yearly conference called SIGINT in May 2009 in Cologne, Germany. Members of the CCC also participate in various technological and political conferences around the planet.
The CCC publishes the quarterly magazine Datenschleuder (data catapult), and the CCC in Berlin also produces a monthly radio show called Chaosradio which picks up various technical and political topics in a two-hour talk radio show. The program is aired on a local radio station named Fritz. There is also a podcast spin-off named Chaosradio Express, an international podcast called Chaosradio International (which has been inactive for a couple of years now), and other radio programs offered by some regional Chaos Groups.
Soldier X

Web Site: http://www.SoldierX.com
Estimated Membership: 2000
Description: Founded in 1997. This was Project 25SX or SOLDIERX version 2.5 as it has become known as. This project was to take SOLDIERX back to its roots – information insemination. This idea removed much of the secrecy behind SX and the difficulty to get involved. Anybody who wanted to help with the site was able to. If a piece of work met criteria, it was posted onto the site by one of the admins. This was kind of like an early version of wikipedia for hackers if you think about it. It was all part of a dream RaT had of a site filled with programs and information which people frequented without incurring a charge. Those people learned from the site, and in turn gave back to it. The site would never be the same. If you look at the current site, all people are welcome to contribute to it. It is increasingly apparent that the wheels of Project 25SX are still in motion.
Relationship Designation: Ally
Notes: This group began as a group of game hackers, and evolved over time into the full fledged
Cyber Militia it is today. SOLDIER X was founded by Clinton H. Weir (Kefka/Ordune/Shto) in 1997 as a RPG group known as „SOLDIER“. RaT was appointed as the leader of the group. Other notable members included Blake and RPGMaster. „SOLDIER“ quickly became the largest group as RaT started to get into programming. He got into programming with the help of „MaGuS“, the the infamous creator of the „Fate X“ program series. SOLDIER wanted to make the whole AOL RPG’ing scene completely automated. He decided that they would do this with a test game application he created dubbed „RaT Fighter 1.0 Beta“. The program was a huge success and „RaT Fighter 1.0″ was eventually created. After his creation was finished, he was pleased that the games in the RPG scene now had the option to be automated – so he worked with his fellow programmers to decide what should be done next.
Anonymous

Web Site: http://www.AnonServ.org
Estimated Membership: 10,000
Description: Anonymous is the second largest hacker group of this kind in the world, and they have been responsible for some of the most historical cyber actions and battles ever. Anonymous is a trans-national and global organization with members in over 100 countries around the world.
Relationship Designation: Allied Group
Notes: While I have listed Anonymous as a Cyber Militia, it is a concensus building co-op. The leaders as much as they exist are primarily the people who run the network platforms upon which Anonymous acts. That said, Anonymous does have many Cyber Militia’s with a more martial organization who do fight under their banner, and their operations are vast and well organized attacks. By offering dozens of different groups and tens of thousands of individuals the unprecedented opportunity to wage cyberwar in a co-ordinated fashion, they meet the criteria of being a Cyber Militia.
Estonian Cyber Defence League

Web Site: http://www.dw-world.de/dw/article/0,,14968102,00.html
Estimated Membership: 1000
Description: In 2007, when Estonia’s government, financial and media computer networks were attacked by unknown Russian hackers following the government’s decision of relocating a Soviet war memorial, it must have been hard to believe that something good would come from it at the end. With that attack, Estonia became the first country ever to actually be engaged in a cyberwar, but that didn’t make them despair. If anything, that incident was what spurred them to institute their own Cyber Defense League – an organization that gathers computer scientists, programmers, software engineers and cybersecurity specialists and would, in time of war, be under the direct command of the military.
Relationship Designation: Neutral
Notes: Estonia, often referred to as „E-stonia,“ is one of the most connected nations of the planet - it’s a place where three quarters of the population use the Internet and nearly all of the 1.3 million people pay their taxes online. The tiny Baltic country was not only the first in the world to enable its citizens to vote online – and as of earlier this year, it now it has its own wired troops too. The new Cyber Defense League was created in response to massive cyberattacks that Estonia sustained four years ago this month. In April 2007, dozens of Estonian financial, media and government websites were rendered unusable for nearly two weeks.
This particular Cyber Militia is unique in that it is now commanded by approximately 100 full time cyber soldiers in the Estonian military. Therefore there is no question of government invovement with this group. My sense is this group will be primarily concerned with defensive measures and in any case it’s most natural enemies will probably come from Russia. However this group could conceivably become a true and potent adversary if there is ever an „Op Estonia“.
Albanian Cyber Army

Web Site: http://www.facebook.com/Albanian.CyberWar
Estimated Membership: 500
Description: What can you say, rabidly nationalistic, pro-Kosovo – and extremely anti-Serbian.
Relationship Designation: Neutral
Notes: This group is small and sort of shadowy. There is a known roster of leaders, and many member followers. Their political motivations are crystal clear, they love Kosovo Independence and hate Serbia, Greece and Macedonia with a passion. They have been responsible for a handful of high profile hacks, and I think they bear watching as a possible future force. I see no possible attack vector between our groups.
Peoples Liberation Front

Web Site: http://www.PeoplesLiberationFront.org
Estimated Membership: 1000
Description: Formed in 1985. A highly organized militant group of hackers who use the original American Militia form of organization. While members are free to come and go and sign up for any Op they want, once signed on to an action there is a tight command and control structure based around commissioned officers known as Commanders. Politically motivated, this dedicated group primarily fights for freedom of information, speech – and expression. This group is transnational and global, with members in over 50 countries. Founded in 1985 this one of the oldest Cyber Militias in the world.
Relationship Designation: N/A
Notes: This small but incredibly potent group contains some of the best hackers in the western world, and is most famous for small and surgical, yet incredibly effective actions around the world on behalf of freedom and justice. The group is diversified into various units dedicated to intelligence, penetration – DDoS attacks and more. This group has a particular expertise in counter intelligence, cyber warefare – and mass media dissemination. The PLF played an important role in the 2011 world wide uprisings which have been termed the Transnational Global Cyber Insurgency; that saw major operations in Tunisia, Algeria, Egypt, Libya, Syria, Ivory Coast – and Yemen just to name a few. This group comes at it’s enemies from every direction at once, and is known for eviscerating entire government networks litteraly over night.
Honker Union of China

Web Site: http://www.ChinaHonker.com
Estimated Membership: 25,000
Description: Formed in 1999 in response to the United States bombing of the Chinese embassy in Belgrade, Yugoslavia. HUC is a group known for hacktivism, mainly present in Mainland China. Literally the name means „Red Guest“, as compared to the usual Chinese transliteration of hacker (hēikè, literally Black Guest as in black hat). The The Honker Union of China is a nationalistic group bent on defending the Government of China from all enmeis both perceived and actual. They are also the largest known Cyber Militia in the world.
Although there is no evidence of Chinese government oversights of the group, with the official
government stance against cyber crime of any kind, the Honker Union and other freelance Chinese hackers have a complex relationship with the Chinese government. Greg Walton noted in his studies that Chinese government has been able to use the Honker Union as a „proxy force“ when Beijing’s political goals converge with the group’s nationalist sentiment. He also noted instances of members profited off the Chinese government for their skills and the Chinese government recruited members into security and military forces. Finally, Greg Walton pointed out that there are some calls within the group to be officially recognized and integrated into the Chinese government.
Relationship Designation: Potential Adversary
Notes: The HUC is the driving force of nationalistic hacking in China today. An amalgamation of
several earlier groups, they continue to grow and add members and absorb rival groups at an
astonishing rate. I personally rate this group as the single most powerful cyber warfare force on the planet. This cyber militia is listed as a potential adversary because of the PLF’s Dark Operations Snow Lion and Red Dragon, both of which will pit us directly against the Chinese Government and the PLA.
Members have launched a series of attacks on websites in the United States, mostly government-related sites. They also routinely target pro-Tibetan Freedom groups and individual activists. The name also suggests that a hacker in red, the color of the Communist party, is in combat with hackers in the dark. The HUC recently joined together with the Red Hacker Alliance to become the single largest hacker force on the planet.
Iranian Cyber Army

Web Site: http://iraniancyberarmy.tumblr.com
Estimated Membership: 5000
Description: Ultra Nationalist hackers who support the current Iranian regime. They have conducted dozens of high profile and very destructive cyber raids in the last few years.
Relationship Designation: Enemy
Notes: A Google search will reveal the details of the most recent high profile attacks by this group. The PLF became aware of this group shortly after we joined with Anonymous in Operation Iran. I sent them a personal appeal to leave off and join us instead, their reply was received a half hour later in the form of massive attacks upon the web assets of the PLF and Anon Ops. It is believed that the IRC receives considerable assistance from the Revolutionary Gaurd Cyber Defense Command. The Iranian Cyber Army is a potent and effective enemy and should be treated with a high level of respect and caution. The IRC is known to make use of huge bot-nets to launch devestating DDoS attacks.







 Now we have some hardcore Linux Magazines which are highly targeted to the professional Linux User. When it comes to computer security and hacking, Linux is the heart and soul of hacking and hackerdom in general. These magazines focus on Linux on a whole and explore the OS with respect to articles on all levels of developing and using Linux and the software that runs on it, including everything from how to write device drivers to how to edit photos with GIMP.
Now we have some hardcore Linux Magazines which are highly targeted to the professional Linux User. When it comes to computer security and hacking, Linux is the heart and soul of hacking and hackerdom in general. These magazines focus on Linux on a whole and explore the OS with respect to articles on all levels of developing and using Linux and the software that runs on it, including everything from how to write device drivers to how to edit photos with GIMP.

 As a special nod to
As a special nod to  When it comes to hacking, every other guy tends to tape the "hacker" word with his name/codename without even realizing its significance. Then there is Facebook ...Have a look at it -
When it comes to hacking, every other guy tends to tape the "hacker" word with his name/codename without even realizing its significance. Then there is Facebook ...Have a look at it -