This article is a revised and a more advanced version of what we learned in the post "Facebook Cookie Stealing And Session Hijacking", before i get started, i would like to share that i have just passed my CCNP route examination with 95.3 percent and i am preparing for my CCNP switch examination therefore i would not be able to post for a while, however our Cheif Editor "Dr Sindhiya Junjeo" will continue to update you with latest hacking news until i return. So Let's get back to the tutorial.
In our previous post, "Facebook Cookie Stealing And Session Hijacking" i used a packet sniffer called "Wireshark" to capture packets on a wireless network and finally captured facebook's authentication cookie and replaced the victims authentication cookie with our own authentication cookie allowing us to hack the facebook account. However this post would be more related to hacking a facebook account on a LAN with ARP Poisoning or Man in the middle attack.
Lan Sniffing - Core Concepts
- If you are sniffing on a local area network (LAN), first of all you should make sure that your Network card is in the promiscuous mode.
- Next up you should know the difference between a hub and a switch based network, in case of a hub based network a normal packet sniffer would do the job, however in case of a switch based network we would need to launch an attack called "ARP Poisoning attack" or "Man in the Middle attack" in order to route the victims traffic through us.
Before reading this tutorial I would recommend you to part1, part2 and part 3 of my Gmail Session Hijacking and Cookie stealing series, So you could have better understanding of what I am doing here.
Logic And Methodology:
The tutorial is divided in to three main steps:
Step 1
First of all we would use "ARP Poisoning" or "Man In the Middle Attack" in order to poison victims "ARP CACHE" and route all the traffic through our computer.
Step 2
Since all the traffic would be rotued through our computer, we would simply launch a packet sniffer (Wireshark) and capture the authentication cookies for facebook.
Step 3
Finally we would replace the victims authentication cookie with our cookies and therefore hacking into victims Facebook account.
Tools
Hack A Facebook Account [ARP Poisoning] {STEP 1 }
Step 1 - Download "Cain and Abel" from the link above and launch it.
Step 2 - Turn on the sniffer by clicking on the Green button at the top, Next scan for the Mac Addresses by clicking on the plus sign (+) at the top.
Step 3 - Once you have scanned all the Mac Addresses and IP addresses, it's time to perform the Man In the middle attack. For that, Click on the APR tab at the bottom and then click on the white area in the top frame. This will turn the "+" sign into blue color.
Step 4 - Next click on the "+" sign, lists of hosts will appear, select the hosts which you want to intercept the traffic between. In my case at the left side would be my default gateway and on the right would be my victim hosts.
Step 5 - Click ok and then finally click the "Yellow Button" just under the file menu of "Cain and abel", Now it will start poisoning the routes in a short span of time and you would start to see traffic being captured by cain and abel.
Monitor a Facebook Account from any where in the world
Hack A Facebook Account [Packet Sniffing Wireshark] {STEP 2}
So, since we have already poisoned victim's ARP Cache, all the traffic going from the victim to the router will be captured by our packet sniffer (Wireshark). But before we capture the cookie, i would like to explain briefly regarding "Facebook Authentication Cookies".
Facebook Authentication Cookies
Well, at the time i wrote the tutorial "Facebook Cookie Stealing And Session Hijacking" Facebook used "Datr" as their authentication cookie, Now facebook uses two cookies instead of one, namely "c_user" and "xs" for authenticating a user. Therefore we would need to capture both of these cookies and replace them with our cookie to hack a facebook account. So here is how you would capture authentication cookies with facebook.
Step 1 - First of all download wireshark from the official website and install it.
Step 2 - Next open up wireshark click on analyze and then click on interfaces.
Step 3 - Next choose the appropriate interface and click on start.
Step 4 - Continue sniffing for around 10 minutes.
Step 5 - After 10minutes stop the packet sniffing by going to the capture menu and clicking on Stop.
Step 6 - Next set the filter to http.cookie contains “datr” at top left, This filter will search for all the http cookies with the name datr, And datr as we know is the name of the facebook authentication cookie.
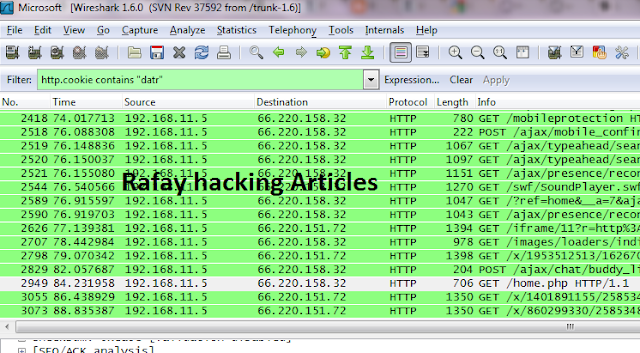
Step 7 - Next right click on it and goto Copy - Bytes - Printable Text only.
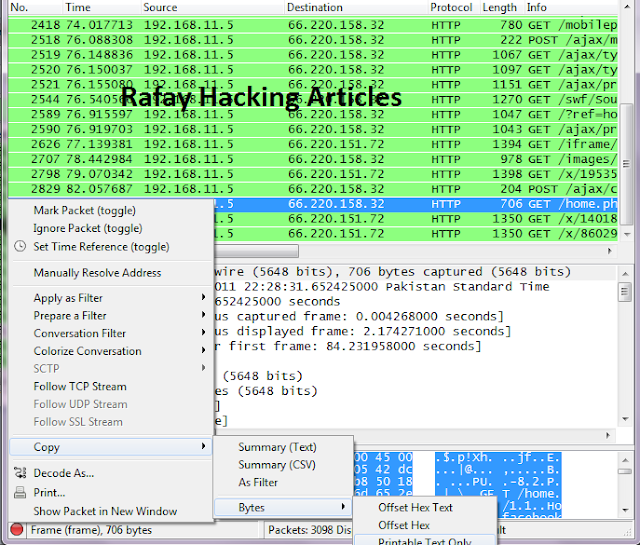
Step 8 - Now you would see lots of cookie values, however c_user and xs would be the only ones of our interest. Copy both of the values in a notepad.
Hack A Facebook Account [Cookie Editing] {Step 3}
Now, finally it's time to hack a facebook account by using the cookie values we captured, for this purpose you would need a cookie editor, I will use a firefox addon called "Cookie Manager" to replace the cookies.
Step 1
First of all open up firefox and browse to http://facebook.com.
Step 2
Next open up the cookie manger (Tools - CookieManager+)
Next open up the cookie manger (Tools - CookieManager+)
Step 3
Next click the "add" button. Fill in the following values: (Take a look at the screenshots below for more clarification)
Next click the "add" button. Fill in the following values: (Take a look at the screenshots below for more clarification)
For Authentication Cookie: c_user
Name: c_user
Value: The value of the cookie that was captured.
Host: .facebook.com
For Authentication Cookie: xs
Name: xs
Value: The value of the cookie that was captured.
Host: .facebook.com
Step 4 -
Next click on the save button, Finally you just need to refresh your page and you would be logged in to the victims account, thus you have hacked a facebook account by session hijacking attack.
Note: This Attack will only work if victim is on a http:// connection and even on https:// if end to end encryption is not enabled.
I hope you have enjoyed the tutorial as much as i have enjoyed while making it, if you have any questions feel free to ask, Feel free to share it with your friends so they can know the dangers of browsing over a http connection.
P.S: If you would like to learn more methods to hack in to facebook account, kindly refer my Facebook Hacking Course