How to block UltraSurf on Squid & Firewall: Ultra Surf Proxy Bypass Finally Blocked Successfully
In most of the organizations, proxy & firewall bypassing is one of the major problem. Few days back the management gave me one task to block ULTRASURF from our SQUID proxy & Firewall. The testing was successful & would like to share it with all you guys also.
First of all I would like to explain all my finding on, how ultra surf works, which IP it uses and on which port it works. For this we have done 2 things. Capture the packets on eth port with ETHEREAL & analyse the log report on both SQUID & FIREWALL.
Ultrasurf set an encrypted connection with remote server. Now question arises is how my computer originates an encrypted tunnel to some remote server. Actually Ultrasurf sets up a local proxy on client machine with default port 9666. Now to create a tunnel we need only 4 things... source IP, source port, destination IP & destination port. Source IP will be clients machine IP & source port will be default 9666. The destination IP is random IP and port will be 443 (most of the time). Now this 443 port is responsible to encrypt the tunnel, as its SSL port and all traffic moves via this port will be encrypted. Its the same port on which HTTPS works. So its not at all possible to block 443 for destination.

Ultrasuf search for proxy servers list OR we can say the destination IP address with one of the following method:
- Proxy server list saved in cache of the local temporary folder
- Encoded IP list of fresh proxy servers updated in local DNS by external DNS
- Document which contains active & live list of proxy servers uploaded on GOOGLE DOCS
- List already inbuilt in the ultrasurf. This list updated in every new version
- If a single proxy server discovered by ULTRASURF, it can auto discover all other proxy servers with the help of this server
Now while capturing the packets and analysis the logs, we found that most of the proxy servers are on 204.0.0.0, 65.0.0.0 & 72.0.0.0 subnet. Now here we came to this conclusion that if we block all these 3 subnets for class A...... means for subnet mask 255.0.0.0, none of the server will be reachable and ultrasurf will be blocked on squid. I thought to search some more research work related to ULTRASURF done by other IT GEEKS. after 5 min of googling, I found one wonderful script created by SACHIN RAJ. According to that script, it will block all IP based browsing in the SQUID proxy. Its the same logic on which we were working. The only difference was we are going to block only 3 subnets. After so many discussion ith my internal server admins, we implemented the script created by Sachin.
Add the below lines in the squid.conf file
vi /etc/squid/squid.conf
Add the below lines in the top of all access lists
acl ipacl url_regex http://[0-9]*\.[0-9]*\.[0-9]*\.[0-9]*
http_access deny ipacl
acl numeric_IPs url_regex ^[0-9]+.[0-9]+.[0-9]+.[0-9]+
http_access deny numeric_IPs
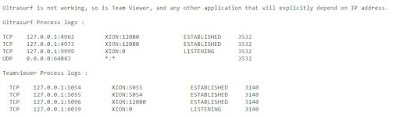
The only drawback is all the apps and softwares which are explicit depends on IP will also blocked. Only the hostname based apps and link will work. We test TEAMVIEWER & it got blocked. Before assigning the partner ID, it tries to ping the keep alive server. After enabling the script, the ping got failed. Check the above screen shot.

Now on firewall, we do not have to explore much. Almost every firewall supports signature based blocking under IPS Signatures and it includes all major tools & softwares. Here I would like to mention that only signature based blocking not work 100%, so you also need to block the proxy server list for better blocking on firewall. All 3 subnets mentioned earlier in this article. Thanks a lot to Shankar Yadav for such a smooth implementation. Only need to enable it carefully and BOOOOMMM ..... ULTRASURF BLOCKED on firewall.
I can not disclose the firewall installed due to security concern, but I will explain how we enabled it on firewall. Shankar's task was to stop ultrasurf, and my task was to update the latest proxy server lists and bypass the firewall. After 2 days of full fledged testing, we came to conclusion that there is some issue with the existing firewall IOS as even after enabling signature based bocking, ultrasurf was working perfectly. The reason was, old IOS does not supports the latest version ULTRASURF signatures. So we plan to update the IOS and after that we implemented 2 things to block ULTRASURF completely. That is IPS signature based blocking & all 3 subnet blocking mentioned earlier. After this when we checked......... we found that we successfully achieved our goal. OH MY GOSH......the proxy tool named as DIGITAL WEAPON against China's great firewall by http://www.wired.com we blocked it successfully on our firewall.











No comments:
Post a Comment