Published on Dec 19, 2012
http://www.sophos.com/threatreport Join Richard Wang, Director of Threat Research at Sophos to learn about threats you should keep an eye on now and into the new year. He'll discuss new attack platforms and the changing threats, protection strategies to combat these threats, blackhole and ransomware, and security predictions for 2013.





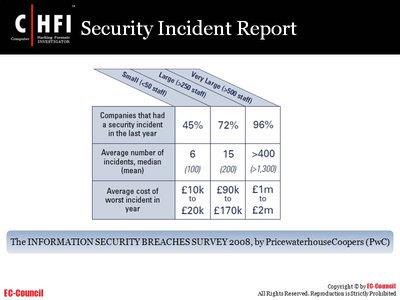
![Blackhat USA 2012 [2012, ENG] Blackhat USA 2012 [2012, ENG]](http://i53.fastpic.ru/big/2013/0107/aa/38d7caef7e2a9bfecadaae8bc73716aa.jpg)
![Blackhat USA 2012 [2012, ENG] Blackhat USA 2012 [2012, ENG]](http://i54.fastpic.ru/big/2013/0107/bb/cba90d017dacd88b0f050cedc4a9a7bb.jpg)
![Blackhat USA 2011 [2011, ENG] Blackhat USA 2011 [2011, ENG]](http://i51.fastpic.ru/big/2013/0107/98/b5b90c10c219a85def4d0904dfa51898.jpg)
![Blackhat USA 2011 [2011, ENG] Blackhat USA 2011 [2011, ENG]](http://i54.fastpic.ru/big/2013/0107/a5/d0cd48f060e08abaf97c52b31e0a48a5.jpg)











