Ethical Hacking CEHv7: Videos, Tools and Tutorials Free Download | 16.25 GB

Ethical Hacking CEHv7: Videos, Tools and Tutorials | 16.25 GB
Genre: eLearning
CEHv7 provides a comprehensive ethical hacking and network security-training program to meet the standards of highly skilled security professionals. Hundreds of SMEs and authors have contributed towards the content presented in the CEHv7 courseware. Latest tools and exploits uncovered from the underground community are featured in the new package.
CEH v.7 provides comprehensive information on on information security. Experience hundreds of businesses and high-security experts have contributed to the content presented in CEH v. 7 courses. This course provides the latest hacking tools and techniques.
Laboratory tests can help you understand:
How is the collection of information
is being scanned as
cracked as account passwords
How do trojans, backdoors, viruses and worms
How does a buffer overflow in programs
How is session hijacking
as DoS attacks are carried out
as hacked Web servers
How are SQL-injection
as wireless networks are attacked
as cost intrusion detection systems, firewalls and antivirus programs
as test system for penetration
How is the collection of information
is being scanned as
cracked as account passwords
How do trojans, backdoors, viruses and worms
How does a buffer overflow in programs
How is session hijacking
as DoS attacks are carried out
as hacked Web servers
How are SQL-injection
as wireless networks are attacked
as cost intrusion detection systems, firewalls and antivirus programs
as test system for penetration
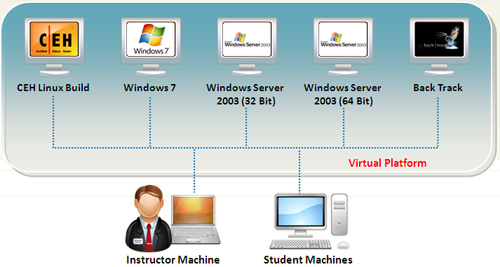
Module 00 - Lab Setup Demos
Module 01 - Introduction to Ethical Hacking
Module 02 - Footprinting and Reconnaissance
Module 03 - Scanning Networks
Module 04 - Enumeration
Module 05 - System Hacking
Module 06 - Trojans and Backdoors
Module 07 - Viruses and Worms
Module 08 - Sniffers
Module 09 - Social Engineering
Module 10 - Denial of Service
Module 11 - Session Hijacking
Module 12 - Hacking Webserver
Module 13 - Hacking Web Applications
Module 14 - SQL Injection
Module 15 - Hacking Wireless Networks
Module 16 - Evading IDS, Firewalls and Honeypots
Module 17 - Buffer Overflows
Module 18 - Cryptography
Module 19 - Penetration Testing










No comments:
Post a Comment