- The NULL session is used on Windows computers via the Inter-Communication Process (IPC$) to allow the viewing of shared resources.
- This connection is made without a username or password.
- An attacker will use the NULL session to enumerate user information from the target.
- From command prompt enter the following syntax: net use \\Target IP Address\IPC$ ""/u:""
- When successful, the result will show The command completed successfully and this is not logged in the System Event Log.
Learn How to Establish a NULL Session
Learn How to Scan all open TCP and UDP ports using VISION
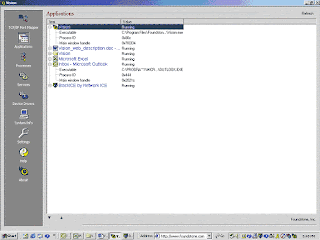
Vision, a host based Forensic Utility is the GUI successor to the well-known freeware tool, Fport. This innovative new product from Foundstone shows all of the open TCP and UDP ports on a machine, displays the service that is active on each port, and maps the ports to their respective applications. Vision allows users to access a large amount of supplementary information that is useful for determining host status by displaying detailed system information, applications running, as well as processes and ports in use.
Key Features
- Interrogate ports and identify potential "Trojan" services by using the "Port Probe" command in the port mapper. Using "Port Probe", Vision will enable you to send a customized string of information to the port. Based on the response from the port, a determination can be made to either kill the port, using the "Kill" command, or leave it as is.
- View system events by sorting by application, process, service, port, remote IP, and device drivers in ascending or descending order.
- Identify and review detailed information about Services and Devices to determine if they are Running or Stopped.
List Applications Running
List Services Running

List Devices Running


Faq
Q. Will Vision work on Windows 9x, Me, or XP?
A. Vision will not work on Windows 9x, or Me. It will work with Windows XP.
Q. I get “Must be Admin” error when trying to launch. I am the Administrator, so what’s the problem?
A. Check to ensure that nbt binding is enabled. In NT 4 this is done in your network interface bindings. Under Win2k check to ensure that you have the TCP/IP Netbios helper enabled.
System Requirements
- NT 4/ Win 2000
- NT 4 needs psapi.dll
- 800x600 res. minimum
- 256 colors min
- 32MB
SOURCE: http://www.foundstone.com
Simple security audit & Penetration test tool HackBar 1.4.2 download for free: Its Add-ons for Firefox
Version 1.4.2
Works with Firefox: 1.5 – 3.6.*
Updated May 13, 2009
Developer Johan Adriaans
Rating Rated 5 out of 5 stars
# In general
This toolbar will help you in testing sql injections, XSS holes and site security. It is NOT a tool for executing standard exploits and it will NOT teach you how to hack a site. Its main purpose is to help a developer do security audits on his code. If you know what your doing, this toolbar will help you do it faster. If you want to learn to find security holes, you can also use this toolbar, but you will probably also need a book, and a lot of google :)
# The advantages are:
- Even the most complicated urls will be readable
- The focus will stay on the textarea, so after executing the url (ctrl+enter) you can just go on typing / testing
- The url in textarea is not affected by redirects.
- I tend to use it as a notepad :)
- Useful tools like on the fly uu/url decoding etc.
- All functions work on the currently selected text.
# Load url ( alt a )
This loads the url of the current page into the textarea.
# Split url ( alt s )
When this button is clicked, the url/text in the textarea will be split into multiple lines using the ? and & character
# Execute ( alt x, ctrl enter )
This will execute the current url in the textarea, i mostly use ctrl+enter
# INT -1 ( alt - )
First select a number in the textarea and press this button, the number will be lowered by 1 and the url will be loaded.
# INT +1 ( alt + )
Again first select a number in the textarea and press this button, 1 will be added to the number and the url will be loaded.
# HEX -1 ( control alt - )
First select a number in the textarea and press this button, the number will be lowered by 1 and the url will be loaded.
# HEX +1 ( control alt + )
Again first select a number in the textarea and press this button, 1 will be added to the number and the url will be loaded.
# MD5 Hash ( alt m )
this is a standard hashing method, often used as an encryption method for passwords. It will MD5 hash the currently selected string.
# SHA-1/256
this is a standard hashing method, often used as an encryption method for passwords. It will SHA-1/256 hash the currently selected string.
# MySQL CHAR() ( alt y )
If quotes are escaped but you did find an SQL injection thats exploitable, you can use this button to convert lets say:
load_file('/etc/passwd') --> load_file(CHAR(47, 101, 116, 99, 47, 112, 97, 115, 115, 119, 100))
Thus omiting the use of quotes to load a file.
You can also use this on
WHERE foo LIKE ('%bar%') --> WHERE foo LIKE (CHAR(37, 98, 97, 114, 37))
# MsSQL CHAR() ( alt q )
Same story as MySQL CHAR(), MsSQL has a slightly different CHAR syntax
--> WHERE foo LIKE ( CHAR(37) + CHAR(98) + CHAR(97) + CHAR(114) + CHAR(37))
# Base64 encode / decode
Base64 encoding ( UU ) is often used to store data (like a return url etc.) This will help you to read those values.
# URLencode / decode
This will encode or decode the currently selected characters to url safe characters. I mostly use it to end a query with # (%23) when in a pseudo path where i cant use /* or --
And lots more ;) Go test it!
Learn How to Scan open ports using Angry IP Scanner
From the Angry IP scanner software enter the target IP address.


Once the scan has completed a window will appear identifying the results. Click OK.
In this example:
- Port 21 (FTP [File Transfer Protocol]) is open.
- Port 80 (Web) is open.
- Port 139 (Windows Share) is open.
- Port 445 (Windows Share) is open.
 Right-click on the IP address to bring up a menu; then select OPEN COMPUTER, then IN EXPLORER.
Right-click on the IP address to bring up a menu; then select OPEN COMPUTER, then IN EXPLORER.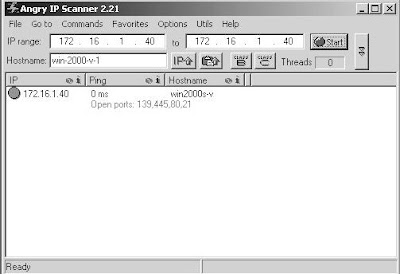
In this example, the results revealed the following:
- The Database directory is shared.
- The Downloads directory is shared.
- The Personal directory is shared.
- There may be Printers shared on the target.
- The Windows scheduler is running and may have tasks that can be modified.
 If the shares ask you for a username/password when attempting to access them, initiate a NULL session and try again.
If the shares ask you for a username/password when attempting to access them, initiate a NULL session and try again.EC - Council CEH Certified Ethical Hacker v7 Training - OnDemand Learning (3 DVD)

EC-Council CEH Certified Ethical Hacker v7 Training - OnDemand Learning (3 DVD)
English | 3 DVD | ISO | 5.36GB
Genre: eLearning
This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems. Students will begin by understanding how perimeter defenses work and then be lead into scanning and attacking their own networks, no real network is harmed. Students then learn how intruders escalate privileges and what steps can be taken to secure a system.
Students will also learn about Intrusion Detection, Policy Creation, Social Engineering, DDoS Attacks, Buffer Overflows and Virus Creation. When a student completes the course they will have hands on understanding and experience in Ethical Hacking. This course prepares you for EC-Council Certified Ethical Hacker exam 312-50
Career Academy is an EC-Council endorsed training provider. We have invited the best security trainers in the industry to help us develop the ultimate training and certification program which includes everything you will need to fully prepare for and pass your certification exams. This officially endorsed product gives our students access to the exam by providing you with an Authorization Code. The EC-Council Authorization Code can be used at any Prometric center, this Authorization Code is required and mandatory for you to schedule and pay for your exam. Without this Authorization Code, Prometric will not entertain any of your requests to schedule and take the exam. See our Joint Press Release with EC-Council. Note: The cost of the exam is not included in this package.
Mentor: Eric Reed - EC-Council Master Certified Instructor, CEH, CHFI, ECSA/LPT, CISSP, MCT, MCSE: Security
Module 00 - Student Introduction
Module 01 - Introduction to Ethical Hacking
Module 02 - Footprinting and Reconnaissance
Module 03 - Scanning Networks
Module 04 - Enumeration
Module 05 - System Hacking
Module 06 - Trojans and Backdoors
Module 07 - Viruses and Worms
Module 08 - Sniffers
Module 09 - Social Engineering
Module 10 - Denial of Service
Module 11 - Session Hijacking
Module 12 - Hacking Webservers
Module 13 - Hacking Web Applications
Module 14 - SQL Injection
Module 15 - Hacking Wireless Networks
Module 16 - Evading IDS, Firewalls, and Honeypots
Module 17 - Buffer Overflow
Module 18 - Cryptography
Module 19 - Penetration Testing
More info:
_http://www.careeracademy.com/ceh-training-cbt-bootcamp-certified-ethical-hacker-cehv7.aspx
Download:
http://shareflare.net/download/56398.52923371cee9bbd0d0d7c2675ccf/cacehv7.part1.rar.html
http://shareflare.net/download/92737.939c47dd4f1e6f2131a8b3371f9d/cacehv7.part2.rar.html
http://shareflare.net/download/56193.56b1002c14142726cb921d311571/cacehv7.part3.rar.html
http://shareflare.net/download/64768.66c5946b9d4f666db4483f347814/cacehv7.part4.rar.html
http://shareflare.net/download/74877.7494783bfbfe7650a1ee965ef2eb/cacehv7.part5.rar.html
http://shareflare.net/download/08386.00f6273c2f40a070ab64c1635895/cacehv7.part6.rar.html
http://shareflare.net/download/28069.22630e11fb01fd87e33177357673/cacehv7.part7.rar.html
Mirror 1:
http://extabit.com/file/27aurg9hj9aok/cacehv7.part1.rar
http://extabit.com/file/27aurg9hj9apw/cacehv7.part2.rar
http://extabit.com/file/27aurg9hjam38/cacehv7.part3.rar
http://extabit.com/file/27aurg9hjam1w/cacehv7.part4.rar
http://extabit.com/file/27aurg9hjam7o/cacehv7.part5.rar
http://extabit.com/file/27aurg9hja9g4/cacehv7.part6.rar
http://extabit.com/file/27aurg9hja9ec/cacehv7.part7.rar
Mirror 2:
http://ryushare.com/29ed7e1fc9c9/cacehv7.part1.rar
http://ryushare.com/2904a97ab9e1/cacehv7.part2.rar
http://ryushare.com/281bd4d5a9c5/cacehv7.part3.rar
http://ryushare.com/2733003099cb/cacehv7.part4.rar
http://ryushare.com/2733003099ca/cacehv7.part5.rar
http://ryushare.com/29ed7e1fc9cc/cacehv7.part6.rar
http://ryushare.com/2904a97ab9e8/cacehv7.part7.rar
Career Academy is an EC-Council endorsed training provider. We have invited the best security trainers in the industry to help us develop the ultimate training and certification program which includes everything you will need to fully prepare for and pass your certification exams. This officially endorsed product gives our students access to the exam by providing you with an Authorization Code. The EC-Council Authorization Code can be used at any Prometric center, this Authorization Code is required and mandatory for you to schedule and pay for your exam. Without this Authorization Code, Prometric will not entertain any of your requests to schedule and take the exam. See our Joint Press Release with EC-Council. Note: The cost of the exam is not included in this package.
Mentor: Eric Reed - EC-Council Master Certified Instructor, CEH, CHFI, ECSA/LPT, CISSP, MCT, MCSE: Security
Module 00 - Student Introduction
Module 01 - Introduction to Ethical Hacking
Module 02 - Footprinting and Reconnaissance
Module 03 - Scanning Networks
Module 04 - Enumeration
Module 05 - System Hacking
Module 06 - Trojans and Backdoors
Module 07 - Viruses and Worms
Module 08 - Sniffers
Module 09 - Social Engineering
Module 10 - Denial of Service
Module 11 - Session Hijacking
Module 12 - Hacking Webservers
Module 13 - Hacking Web Applications
Module 14 - SQL Injection
Module 15 - Hacking Wireless Networks
Module 16 - Evading IDS, Firewalls, and Honeypots
Module 17 - Buffer Overflow
Module 18 - Cryptography
Module 19 - Penetration Testing
More info:
_http://www.careeracademy.com/ceh-training-cbt-bootcamp-certified-ethical-hacker-cehv7.aspx
Sceenshot:


Download:
http://shareflare.net/download/56398.52923371cee9bbd0d0d7c2675ccf/cacehv7.part1.rar.html
http://shareflare.net/download/92737.939c47dd4f1e6f2131a8b3371f9d/cacehv7.part2.rar.html
http://shareflare.net/download/56193.56b1002c14142726cb921d311571/cacehv7.part3.rar.html
http://shareflare.net/download/64768.66c5946b9d4f666db4483f347814/cacehv7.part4.rar.html
http://shareflare.net/download/74877.7494783bfbfe7650a1ee965ef2eb/cacehv7.part5.rar.html
http://shareflare.net/download/08386.00f6273c2f40a070ab64c1635895/cacehv7.part6.rar.html
http://shareflare.net/download/28069.22630e11fb01fd87e33177357673/cacehv7.part7.rar.html
Mirror 1:
http://extabit.com/file/27aurg9hj9aok/cacehv7.part1.rar
http://extabit.com/file/27aurg9hj9apw/cacehv7.part2.rar
http://extabit.com/file/27aurg9hjam38/cacehv7.part3.rar
http://extabit.com/file/27aurg9hjam1w/cacehv7.part4.rar
http://extabit.com/file/27aurg9hjam7o/cacehv7.part5.rar
http://extabit.com/file/27aurg9hja9g4/cacehv7.part6.rar
http://extabit.com/file/27aurg9hja9ec/cacehv7.part7.rar
Mirror 2:
http://ryushare.com/29ed7e1fc9c9/cacehv7.part1.rar
http://ryushare.com/2904a97ab9e1/cacehv7.part2.rar
http://ryushare.com/281bd4d5a9c5/cacehv7.part3.rar
http://ryushare.com/2733003099cb/cacehv7.part4.rar
http://ryushare.com/2733003099ca/cacehv7.part5.rar
http://ryushare.com/29ed7e1fc9cc/cacehv7.part6.rar
http://ryushare.com/2904a97ab9e8/cacehv7.part7.rar
EC - Council CEH Certified Ethical Hacker v7.1 OnDemand Learning

CEH Certified Ethical Hacker v7.1 OnDemand Learning
English | ISO | March 2012 | 3.87Gb
Genre: e-learning
This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems. Students will begin by understanding how perimeter defenses work and then be lead into scanning and attacking their own networks, no real network is harmed. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Students will also learn about Intrusion Detection, Policy Creation, Social Engineering, DDoS Attacks, Buffer Overflows and Virus Creation. When a student completes the course they will have hands on understanding and experience in Ethical Hacking. This course prepares you for EC-Council Certified Ethical Hacker exam 312-50
Eric Reed - EC-Council Master Certified Instructor, CEH, CHFI, ECSA/LPT, CISSP, MCT, MCSE: Security
Eric Reed brings more than a decade of IT experience to his expert video instruction. Eric specializes in network penetration testing and digital forensics consultation for large corporations and government sectors. After working for many years in the IT security and training industry as an independent consultant, Eric became co-owner of Immersion Training, LLC. He is currently solely focused on advanced security consulting and education. Eric is an EC-Council Master Certified Instructor and a Microsoft Certified Trainer.
His experience in the public / defense sectors is equally complemented by assignments undertaken for heavyweight world renowned corporations including Yahoo, Xerox, AT&T and Texas Instruments to name but a few. He is imminently qualified in his field in that he holds a string of professional qualifications in Networking to name a few (MCT, MCSE, Cisco, Network+) and IT Security (CIW Security Analyst , Security+, CEI, CEH, CPTE, CDFI, CPTM) besides a bachelor's degree in science.
HomePage: http://www.careeracademy.com/ceh-training-cbt-bootcamp-certified-ethical-hacker-cehv7.aspx
Download:
http://ul.to/g4d87o1m/Career_Academy.part01.rar
http://ul.to/g3vgxmxh/Career_Academy.part02.rar
http://ul.to/zzlzfexg/Career_Academy.part03.rar
http://ul.to/m2htfpcb/Career_Academy.part04.rar
http://ul.to/3tmu7m7c/Career_Academy.part05.rar
http://ul.to/z8aeob07/Career_Academy.part06.rar
http://ul.to/23ar8j3o/Career_Academy.part07.rar
http://ul.to/3u2fzrii/Career_Academy.part08.rar
http://ul.to/5bcwjlgq/Career_Academy.part09.rar
Mirror 1:
http://rapidgator.net/file/3183933/Career_Academy.part01.rar.html
http://rapidgator.net/file/3183929/Career_Academy.part02.rar.html
http://rapidgator.net/file/3183930/Career_Academy.part03.rar.html
http://rapidgator.net/file/3183886/Career_Academy.part04.rar.html
http://rapidgator.net/file/3183987/Career_Academy.part05.rar.html
http://rapidgator.net/file/3183948/Career_Academy.part06.rar.html
http://rapidgator.net/file/3183947/Career_Academy.part07.rar.html
http://rapidgator.net/file/3183847/Career_Academy.part08.rar.html
http://rapidgator.net/file/3183571/Career_Academy.part09.rar.html
Mirror 2:
http://letitbit.net/download/73684.7546f71288c516c109dafcd2b286/Career_Academy.part01.rar.html
http://letitbit.net/download/67252.68405eff9dcd73a3880cf92638e7/Career_Academy.part02.rar.html
http://letitbit.net/download/22374.2f1fde79f5018620a042d315f102/Career_Academy.part03.rar.html
http://letitbit.net/download/79158.736edee1b09169ddc927c1c3d08c/Career_Academy.part04.rar.html
http://letitbit.net/download/07491.06b6e3323beba5feaeaa96b246db/Career_Academy.part05.rar.html
http://letitbit.net/download/88261.8ebb87d0e03455679d10190cd523/Career_Academy.part06.rar.html
http://letitbit.net/download/61688.68b5bde8f69ee605dbe0878dfad1/Career_Academy.part07.rar.html
http://letitbit.net/download/01173.041e0b52db3c1809671f900840d1/Career_Academy.part08.rar.html
http://letitbit.net/download/40994.411be7dac4242857107adcda4c7c/Career_Academy.part09.rar.html
Eric Reed brings more than a decade of IT experience to his expert video instruction. Eric specializes in network penetration testing and digital forensics consultation for large corporations and government sectors. After working for many years in the IT security and training industry as an independent consultant, Eric became co-owner of Immersion Training, LLC. He is currently solely focused on advanced security consulting and education. Eric is an EC-Council Master Certified Instructor and a Microsoft Certified Trainer.
His experience in the public / defense sectors is equally complemented by assignments undertaken for heavyweight world renowned corporations including Yahoo, Xerox, AT&T and Texas Instruments to name but a few. He is imminently qualified in his field in that he holds a string of professional qualifications in Networking to name a few (MCT, MCSE, Cisco, Network+) and IT Security (CIW Security Analyst , Security+, CEI, CEH, CPTE, CDFI, CPTM) besides a bachelor's degree in science.
HomePage: http://www.careeracademy.com/ceh-training-cbt-bootcamp-certified-ethical-hacker-cehv7.aspx
Download:
http://ul.to/g4d87o1m/Career_Academy.part01.rar
http://ul.to/g3vgxmxh/Career_Academy.part02.rar
http://ul.to/zzlzfexg/Career_Academy.part03.rar
http://ul.to/m2htfpcb/Career_Academy.part04.rar
http://ul.to/3tmu7m7c/Career_Academy.part05.rar
http://ul.to/z8aeob07/Career_Academy.part06.rar
http://ul.to/23ar8j3o/Career_Academy.part07.rar
http://ul.to/3u2fzrii/Career_Academy.part08.rar
http://ul.to/5bcwjlgq/Career_Academy.part09.rar
Mirror 1:
http://rapidgator.net/file/3183933/Career_Academy.part01.rar.html
http://rapidgator.net/file/3183929/Career_Academy.part02.rar.html
http://rapidgator.net/file/3183930/Career_Academy.part03.rar.html
http://rapidgator.net/file/3183886/Career_Academy.part04.rar.html
http://rapidgator.net/file/3183987/Career_Academy.part05.rar.html
http://rapidgator.net/file/3183948/Career_Academy.part06.rar.html
http://rapidgator.net/file/3183947/Career_Academy.part07.rar.html
http://rapidgator.net/file/3183847/Career_Academy.part08.rar.html
http://rapidgator.net/file/3183571/Career_Academy.part09.rar.html
Mirror 2:
http://letitbit.net/download/73684.7546f71288c516c109dafcd2b286/Career_Academy.part01.rar.html
http://letitbit.net/download/67252.68405eff9dcd73a3880cf92638e7/Career_Academy.part02.rar.html
http://letitbit.net/download/22374.2f1fde79f5018620a042d315f102/Career_Academy.part03.rar.html
http://letitbit.net/download/79158.736edee1b09169ddc927c1c3d08c/Career_Academy.part04.rar.html
http://letitbit.net/download/07491.06b6e3323beba5feaeaa96b246db/Career_Academy.part05.rar.html
http://letitbit.net/download/88261.8ebb87d0e03455679d10190cd523/Career_Academy.part06.rar.html
http://letitbit.net/download/61688.68b5bde8f69ee605dbe0878dfad1/Career_Academy.part07.rar.html
http://letitbit.net/download/01173.041e0b52db3c1809671f900840d1/Career_Academy.part08.rar.html
http://letitbit.net/download/40994.411be7dac4242857107adcda4c7c/Career_Academy.part09.rar.html
Best Hacking Tool List: Top 10 Hacking Tools and Software
Top 10 Hacking Tools and Software
A Hacking tool is nothing but a device or a piece of software used by any unauthorized user to gain access or to attack any information available on your computer. Hacking tools try to bypass the security systems of any computer in order to gain copy or even to destroy information from its host. Here is a list of what is believed to be among the best of the hacking tools by most hackers. These tools are used only for ethical hacking purposes and are not illegal.
1. Nmap
The tool Network Mapper has gained immense popularity in recent times as it is an open source and a free tool which is used to explore networks and also in security auditing. It is designed to scan networks rapidly. It also copes very well against a single host. Nmap uses IP packets to determine what type of hosts are present in the network along with information on the applications being used by them and also the operating systems that they are running along with their respective versions. In additional to these it also identifies the firewalls being used and many more other characteristics of any given host.
2. Nessus Remote Security Scanner
The Nessus Security Scanner was started by Renaud Deraison in the year 1988 to provide a free remote scanner to the internet community. But since the year 2005 the Nessus Remote Security Scanner has become closed source software although the engine that runs the software is still free of cost.
The Nessus Security Scanner has been the world's most popular scanner being used by well over 75000 organizations world-wide. Many have befitted from this software and it is being used extensively in auditing critical enterprise devices.
3. John the Ripper
John the Ripper commonly known as JTR is a password cracker available for DOS, WIN32, UNIX, OpenVMS and BeOS. Its primary purpose is to detect weak passwords, but at the same time can be very handy to crack passwords also.
4. Nikto
Nikto web scanner as the name suggests is an Open Source web scanner which is capable of performing comprehensive tests on any web server for multiple items, including some of the most potentially dangerous files or CGIs, versions in about 625 servers and version specific problems in about 230 servers.
5. SuperScan
SuperScan is a powerful TCP port scanner, resolver and also pinger. It is a very highly popular port scanning tools made especially for windows users. If you are looking for a substitute to Nmap with a good user interface, then SuperScan is your best bet.
6. p0f
p0f is an extremely versatile passive OS fingerprinting tool. It can identify the operating systems on SYN mode, SYN+ACK mode and also RST+ mode. The p0f software is so versatile that it can fingerprint anything without even making a single active connection to the target system.
7. Wireshark
Wireshark which was formerly known as ethereal is network protocol analyzer or in common terms a sniffer. Wireshark lets you browse and capture the contents of network frames. It is compatible with both windows and linux and is very user-friendly.
8. Yersinia
Yersinia is a hacking tool which is designed to manipulate the weaknesses in different Layer 2 protocols. It pretends like a solid framework for testing and analyzing the systems and networks it is deployed into. Spanning Tree Protocol (STP), Dynamic Trunking Protocol (DTP), Cisco Discovery Protocol (CDP), Hot Standby Router Protocol (HSRP), Dynamic Host Configuration Protocol (DHCP), VLAN Trunking Protocol (VTP), IEEE 802.1q and Inter-Switch Link Protocol (ISL), are some of the protocols which can be implemented.
9. Eraser
Eraser is an advanced security tool for windows used to completely remove any trace whatsoever of any bit of information permanently from the hard drive. This is achieved by continuously overwriting the memory locations where the targeted information was previously available. It works well on all the windows versions till windows xp. Eraser is a free tool which is available under the GNU General Public license.
10. PuTTY
PuTTY is a free software used for implementation of Telnet and SSH for UNIX and WIN32. It is an absolute necessity for any h4x0r to Telnet or SSH without using MS command line clients.
These are the most popular of the hacking tools that are being used widely there are also several other alternatives to these tools so feel free to experiment with other varieties of tools out there. Along with the above a few other software, which are almost similar to the ones mentioned above like LCP, Cain and Abel, Kismet and NetStumbler are also good and handy.
A collection of all the above would give any user enough power to be a good hacker. It is also important to note that the information furnished here is not meant to be used for illegal purposes and also that hacking is a punishable offence in most countries. Use these powerful tools wisely.
About the author: Brianne Walter is a blogger by profession. She loves writing on technology and luxury. Beside this she is fond of gadgets. Recently an article on HTC EVO 3D review attracted her attention. These days she is busy in writing an article on Aventador.
Career Academy - Certified Ethical Hacker v7.1 (CEH) Tools 6 DVDs ( DVD6)

Career Academy - Certified Ethical Hacker v7.1 (CEH) Tools 6 DVDs ( DVD6)
English | DVD6 | ISO | 3.10 Gb
Genre: Video Training
English | DVD6 | ISO | 3.10 Gb
Genre: Video Training
This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems. The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems. Students will begin by understanding how perimeter defenses work and then be lead into scanning and attacking their own networks, no real network is harmed. Students then learn how intruders escalate privileges and what steps can be taken to secure a system. Students will also learn about Intrusion Detection, Policy Creation, Social Engineering, DDoS Attacks, Buffer Overflows and Virus Creation. When a student completes the course they will have hands on understanding and experience in Ethical Hacking. This course prepares you for EC-Council Certified Ethical Hacker exam 312-50
Career Academy is an EC-Council endorsed training provider. We have invited the best security trainers in the industry to help us develop the ultimate training and certification program which includes everything you will need to fully prepare for and pass your certification exams. This officially endorsed product gives our students access to the exam by providing you with an Authorization Code. The EC-Council Authorization Code can be used at any Prometric center, this Authorization Code is required and mandatory for you to schedule and pay for your exam. Without this Authorization Code, Prometric will not entertain any of your requests to schedule and take the exam. See our Joint Press Release with EC-Council. Note: The cost of the exam is not included in this package.
Limited Time Bonus Offer:
Receive our CompTIA Linux+ 2009 Training at No Cost (Value at $595)
It is recommended that students view the Linux+ 2009 course prior to beginning their CEH training.
12 Months Online On-Demand Access (or DVDs) featuring live instructor-led classroom sessions with full audio, video and demonstration components
EC-Council CEH v7.1 Courseware Kit ($595 Value)
A 5 DVD Media Pack containing over 300 of the latest Hacking Tools and Exploits
Intensive Hacking and Counter-Hacking Hands-On demonstration components
2 Official EC-Council CEH Curriculum Manuals
1 EC-Council Ethical Hacker White T-Shirt (XL)
1 EC-Council Logo Backpack
Over 190 CEH Exam Review Questions
Exclusive LearningZone Live Mentor Click for Details (Value at $295)
Help whenever you need it! Exclusive LearningZone - Why wait for email support? Chat Live with our Certified Instructors anytime around the clock (24x7)
Proven technique- Actual Exam Secrets Review
Certification Exam Pass Guarantee
Free 1 Year Upgrade Policy
Certificate of Completion
More:http://www.careeracademy.com/ceh-training-cbt-bootcamp-certified-ethical-hacker-cehv7.aspx
Download:
http://extabit.com/file/2crjlp25h25jb/CEh_v7.1_Volume6.part01.rar
http://extabit.com/file/2crjlp25h25jr/CEh_v7.1_Volume6.part02.rar
http://extabit.com/file/2crjlp25k5k7r/CEh_v7.1_Volume6.part03.rar
http://extabit.com/file/2crjlp25kt36v/CEh_v7.1_Volume6.part04.rar
http://extabit.com/file/2crjlp25ixu6v/CEh_v7.1_Volume6.part05.rar
http://extabit.com/file/2crjlp25iwm1j/CEh_v7.1_Volume6.part06.rar
http://extabit.com/file/2crjlp29t4d93/CEh_v7.1_Volume6.part07.rar
http://extabit.com/file/2crjlp29t4d9j/CEh_v7.1_Volume6.part08.rar
Mirror 1:
http://shareflare.net/download/71377.7e1f8884ee6532c3e1820ef8e015/CEh_v7.1_Volume6.part01.rar.html
http://shareflare.net/download/51861.5f81587b6420dd02dd05b0e42118/CEh_v7.1_Volume6.part02.rar.html
http://shareflare.net/download/16509.1af992c028c7024af6dad894fe2a/CEh_v7.1_Volume6.part03.rar.html
http://shareflare.net/download/77325.7dcb12dbe94424a7b30e717ef94d/CEh_v7.1_Volume6.part04.rar.html
http://shareflare.net/download/15458.1e3a0c4c6a00ddb20c574a234526/CEh_v7.1_Volume6.part05.rar.html
http://shareflare.net/download/25157.29bb7e8472bf03fc978c5e5611b1/CEh_v7.1_Volume6.part06.rar.html
http://shareflare.net/download/78305.7bfde193c1865c4c5ff89049d272/CEh_v7.1_Volume6.part07.rar.html
http://shareflare.net/download/12609.107c3c0b535c9415887cb563dab2/CEh_v7.1_Volume6.part08.rar.html
Mirror 2:
http://letitbit.net/download/39027.382584f51a4339cb5b22b353c926/CEh_v7.1_Volume6.part01.rar.html
http://letitbit.net/download/05917.0e7bc1075d0d872684cf549610e8/CEh_v7.1_Volume6.part02.rar.html
http://letitbit.net/download/92681.9f6c80856371b947e06a732b0cc9/CEh_v7.1_Volume6.part03.rar.html
http://letitbit.net/download/94389.916837dc78cc6aa0b2bda52dce1d/CEh_v7.1_Volume6.part04.rar.html
http://letitbit.net/download/33693.30f79eb068b1d3a04077f681c058/CEh_v7.1_Volume6.part05.rar.html
http://letitbit.net/download/37352.3072c4034b97143a34ed09121a1a/CEh_v7.1_Volume6.part06.rar.html
http://letitbit.net/download/97136.9225f9598ef87c1fd2a2495a963b/CEh_v7.1_Volume6.part07.rar.html
http://letitbit.net/download/72537.7f3744be3608268ace412e92a016/CEh_v7.1_Volume6.part08.rar.html
Information Security: A Manager's Guide to Thwarting Data Thieves and Hackers

Information Security: A Manager's Guide to Thwarting Data Thieves and Hackers
English | ISBN: 0313345589 | 2008 | 188 pages | EPUB | 0,1 MB
Organizations with computer networks, Web sites, and employees carrying laptops and Blackberries face an array of security challenges. Among other things, they need to keep unauthorized people out of the network, thwart Web site hackers, and keep data safe from prying eyes or criminal hands. This book provides a high-level overview of these challenges and more. But it is not for the hard-core IT security engineer who works full time on networks. Instead, it is aimed at the nontechnical executive with responsibility for ensuring that information and assets stay safe and private. Written by a practicing information security officer, Philip Alexander, the book contains the latest information and arms readers with the knowledge they need to make better business decisions.
http://ryushare.com/dbbbe22de96/0313345589_InformSecur.epub
The Web Application Hacker's Handbook 2nd Edition

The Web Application Hacker's Handbook 2nd Edition
PDF | ISBN-10: 1118026470 | 13.52 MB
Web applications are the front door to most organizations, exposing them to attacks that may disclose personal information, execute fraudulent transactions, or compromise ordinary users. This practical book has been completely updated and revised to discuss the latest step-by-step techniques for attacking and defending the range of ever-evolving web applications. You'll explore the various new technologies employed in web applications that have appeared since the first edition and review the new attack techniques that have been developed, particularly in relation to the client side.
Reveals how to overcome the new technologies and techniques aimed at defending web applications against attacks that have appeared since the previous edition
Discusses new remoting frameworks, HTML5, cross-domain integration techniques, UI redress, framebusting, HTTP parameter pollution, hybrid file attacks, and more
Features a companion web site hosted by the authors that allows readers to try out the attacks described, gives answers to the questions that are posed at the end of each chapter, and provides a summarized methodology and checklist of tasks
Focusing on the areas of web application security where things have changed in recent years, this book is the most current resource on the critical topic of discovering, exploiting, and preventing web application security flaws.

Extabit Links
http://extabit.com/file/27b35hpppeysb
Rapidgator mirror
http://rapidgator.net/file/6004359
Gray Hat Hacking The Ethical Hackers Handbook (3rd edition)

Allen Harper, Shon Harris, Jonathan Ness, Chris Eagle, Gideon Lenkey, Terron Williams - Gray Hat Hacking The Ethical Hackers Handbook (3rd edition)
Published: 2011-01-06 | ISBN: 0071742557 | PDF | 720 pages | 13.47 MB
Published: 2011-01-06 | ISBN: 0071742557 | PDF | 720 pages | 13.47 MB
THE LATEST STRATEGIES FOR UNCOVERING TODAY'S MOST DEVASTATING ATTACKS
Thwart malicious network intrusion by using cutting-edge techniques for finding and fixing security flaws. Fully updated and expanded with nine new chapters, Gray Hat Hacking: The Ethical Hacker's Handbook, Third Edition details the most recent vulnerabilities and remedies along with legal disclosure methods. Learn from the experts how hackers target systems, defeat production schemes, write malicious code, and exploit flaws in Windows and Linux systems. Malware analysis, penetration testing, SCADA, VoIP, and Web security are also covered in this comprehensive resource.
Download
http://letitbit.net/download/84924.866471694c7b8cac6a56f6bf6234/2012-04-19-16-0071742557.pdf.html
or
http://vip-file.com/downloadlib/413697571636099584-84924.866471694c7b8cac6a56f6bf6234/2012-04-19-16-0071742557.pdf.html
http://letitbit.net/download/84924.866471694c7b8cac6a56f6bf6234/2012-04-19-16-0071742557.pdf.html
or
http://vip-file.com/downloadlib/413697571636099584-84924.866471694c7b8cac6a56f6bf6234/2012-04-19-16-0071742557.pdf.html
The Basics of Hacking and Penetration Testing

The Basics of Hacking and Penetration Testing
PDF | ISBN-10: 1597496553 | 180 pages | 3.74 MB
The Basics of Hacking and Penetration Testing serves as an introduction to the steps required to complete a penetration test or perform an ethical hack. You learn how to properly utilize and interpret the results of modern day hacking tools; which are required to complete a penetration test. Tool coverage will include, Backtrack Linux, Google, Whois, Nmap, Nessus, Metasploit, Netcat, Netbus, and more. A simple and clean explanation of how to utilize these tools will allow you to gain a solid understanding of each of the four phases and prepare them to take on more in-depth texts and topics. This book includes the use of a single example (pen test target) all the way through the book which allows you to clearly see how the tools and phases relate.

Extabit Links
http://extabit.com/file/27b35fypankc7
Rapidgator mirror
http://rapidgator.net/file/7113468
How To : Preparing for Distributed Denial of Service (DDoS) attacks | White Paper by DELL
An Introduction to DDoS attacks
After emerging in 1999, Distributed Denial of Service (DDoS) attacks have again gained a lot of attention due to recent high-profile attacks by hacktivist groups and extensive media coverage. As a trusted security services provider, Dell SecureWorks has prepared the following high-level brief to provide a basic understanding of these types of attacks, and methods that can be used to mitigate them. Those interested in a more detailed technical analysis should look to the end of this paper for a link to the complete Dell SecureWorks Threat Analysis of DDoS.
DDoS attacks are attempts by one or more adversaries to disrupt availability of a network asset using ultiple attack sources. This can occur at the network layer when available bandwidth is consumed, at the transport layer when processing capacity of in-line network devices is exceeded, or at the application layer when the ability of an application to respond to network requests is exceeded.
Recent high-profile attacks have targeted Web servers at the application layer, where one or more adversaries attempt to take down a website by flooding the Web server with more traffic than it can handle. A successful DDoS attack against a Web server can effectively knock the website offline, making it unavailable to end users and customers. These attacks are most often used to damage businesses whose websites or online assets are a major source of revenue, an indicator of brand value, or critical to business operations. An organization can become a target for any variety of reasons, but the attacks are often used as a form of protest by activists or an attempt to extort a business by essentially holding its website hostage.
Although major DDoS attacks are a rare occurrence for most organizations, they can be very detrimental and attempts cannot be prevented. Because of this, it is important to proactively implement mitigations and practice DDoS incident response plans prior to a DDoS event occurring. The remainder of this brief will outline the steps that a business can take to mitigate the effects of a DDoS attack.
Basic DDoS Preparation
DDoS attacks are possible because the Internet is built from limited consumable resources. If a business had unlimited bandwidth and unlimited computing resources, then an attacker couldn’t feasibly consume all of these resources - but this simply isn’t the case. An organization must balance the amount of resources they are willing to put towards preventing a DDoS attack from occurring with an acceptable level of risk.
Security professionals, especially those well versed in DDoS, can usually help the organization compute the costs associated with the different levels of risk. The more resources (i.e. Web server capacity and Internet bandwidth) an organization has dedicated to their public-facing website, the more difficult it will be for an attacker to consume all available resources. Therefore, the business must determine and understand the level of risk associated with their infrastructure and how easy or difficult it would be for an attack to be successful.
Organizations must consider the varying components of the network architecture during this review, because there are often multiple points of failure that could collapse under the pressure of a DDoS attack. These technologies often come with numerous configuration options and bypass controls that can be set up to align with the security needs and risk tolerance of your organization. As a starting point, determine the weakest link and first point of failure in your network by performing load testing and a system performance review. This analysis highlights areas where investment can be most effective at preventing the downtime that would result from a DDoS attack. It is also critical that a business review and understand the full cost of website downtime, so it can be taken into consideration when calculating how much to spend on the resources to prevent these attacks.
Understanding and agreeing upon these metrics is not a simple task, nor is designing and implementing the right architecture and policies. If your internal resources do not have the necessary time or expertise to perform these tasks, the Dell SecureWorks Security and Risk Consulting (SRC) group can help by evaluating your current environment and providing recommendations that will best meet your needs and budget.
Creating an Incident Response Plan
Internet resources are limited, so complete DDoS prevention is impossible in practice. Therefore, a determined attacker may be able to successfully take down a website built on a very resilient architecture. Nowadays, there are publicly available toolkits that make attacking a target quite simple, so that attacks are not limited to groups with a sophisticated knowledge of networking and architecture design. Thousands of botnets are available for rent on the Internet, providing ample resources for those who would want to disable a public-facing website.
It is for all these reasons that DDoS attack mitigations should be part of the organization’s incident response, crisis response and business continuity plans. Having a plan of action in place is critical to ensure a timely recovery from a successful DDoS attack. This plan of action should be practiced and tested regularly to ensure that everything goes as expected and alterations can be made to improve processes and efficiency.
Because successful attacks can have an impact on multiple business units, all stakeholders need to be made aware of the consequences of DDoS attacks and included in the planning process to ensure their interests are properly represented and protected. Typically, an organization's CIO, CSO, CISO, or Risk Management Officer will ultimately be responsible for ensuring this representation happens, and in the event of an attack that significantly impacts multiple business areas, will likely be the one held accountable for the outcome.
The Dell SecureWorks Security and Risk Consulting team can help organizations build an incident response plan that maps to their environment and staffing model. Their expertise and experience in responding to DDoS attacks can provide insight into best practices and common pitfalls. During a typical DDoS Incident Response Plan engagement, the SRC group can help you:
DDoS attacks cannot be prevented, but organizations can become aware of the threat and work proactively to establish countermeasures and incident response plans to mitigate and minimize the potential impact of a determined and well-resourced attacker. Understanding the adversary's tactics, techniques, and procedures, as well as the options available for mitigating the effects, is vital to establishing a strong security posture and planning a rapid, effective response.
A more detailed technical analysis of DDoS attacks is also available, describing the various types of attacks, common tools and tactics, trends in DDoS, countermeasures, and legal issues. The analysis is targeted towards an audience with a solid understanding of networking.
The report is available at: Threat Analysis: Understanding and Combating DDoS Attacks
Should you have any additional questions about how Dell SecureWorks can help your organization plan for or respond to DDoS attacks, contact your account manager, email info@secureworks.com or call (877) 905-6661.
THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES. THE CONTENT IS PROVIDED AS IS, WITHOUT EXPRESS OR IMPLIED WARRANTIES OF ANY KIND.
After emerging in 1999, Distributed Denial of Service (DDoS) attacks have again gained a lot of attention due to recent high-profile attacks by hacktivist groups and extensive media coverage. As a trusted security services provider, Dell SecureWorks has prepared the following high-level brief to provide a basic understanding of these types of attacks, and methods that can be used to mitigate them. Those interested in a more detailed technical analysis should look to the end of this paper for a link to the complete Dell SecureWorks Threat Analysis of DDoS.
DDoS attacks are attempts by one or more adversaries to disrupt availability of a network asset using ultiple attack sources. This can occur at the network layer when available bandwidth is consumed, at the transport layer when processing capacity of in-line network devices is exceeded, or at the application layer when the ability of an application to respond to network requests is exceeded.
Recent high-profile attacks have targeted Web servers at the application layer, where one or more adversaries attempt to take down a website by flooding the Web server with more traffic than it can handle. A successful DDoS attack against a Web server can effectively knock the website offline, making it unavailable to end users and customers. These attacks are most often used to damage businesses whose websites or online assets are a major source of revenue, an indicator of brand value, or critical to business operations. An organization can become a target for any variety of reasons, but the attacks are often used as a form of protest by activists or an attempt to extort a business by essentially holding its website hostage.
Although major DDoS attacks are a rare occurrence for most organizations, they can be very detrimental and attempts cannot be prevented. Because of this, it is important to proactively implement mitigations and practice DDoS incident response plans prior to a DDoS event occurring. The remainder of this brief will outline the steps that a business can take to mitigate the effects of a DDoS attack.
Basic DDoS Preparation
DDoS attacks are possible because the Internet is built from limited consumable resources. If a business had unlimited bandwidth and unlimited computing resources, then an attacker couldn’t feasibly consume all of these resources - but this simply isn’t the case. An organization must balance the amount of resources they are willing to put towards preventing a DDoS attack from occurring with an acceptable level of risk.
Security professionals, especially those well versed in DDoS, can usually help the organization compute the costs associated with the different levels of risk. The more resources (i.e. Web server capacity and Internet bandwidth) an organization has dedicated to their public-facing website, the more difficult it will be for an attacker to consume all available resources. Therefore, the business must determine and understand the level of risk associated with their infrastructure and how easy or difficult it would be for an attack to be successful.
Organizations must consider the varying components of the network architecture during this review, because there are often multiple points of failure that could collapse under the pressure of a DDoS attack. These technologies often come with numerous configuration options and bypass controls that can be set up to align with the security needs and risk tolerance of your organization. As a starting point, determine the weakest link and first point of failure in your network by performing load testing and a system performance review. This analysis highlights areas where investment can be most effective at preventing the downtime that would result from a DDoS attack. It is also critical that a business review and understand the full cost of website downtime, so it can be taken into consideration when calculating how much to spend on the resources to prevent these attacks.
Understanding and agreeing upon these metrics is not a simple task, nor is designing and implementing the right architecture and policies. If your internal resources do not have the necessary time or expertise to perform these tasks, the Dell SecureWorks Security and Risk Consulting (SRC) group can help by evaluating your current environment and providing recommendations that will best meet your needs and budget.
Creating an Incident Response Plan
Internet resources are limited, so complete DDoS prevention is impossible in practice. Therefore, a determined attacker may be able to successfully take down a website built on a very resilient architecture. Nowadays, there are publicly available toolkits that make attacking a target quite simple, so that attacks are not limited to groups with a sophisticated knowledge of networking and architecture design. Thousands of botnets are available for rent on the Internet, providing ample resources for those who would want to disable a public-facing website.
It is for all these reasons that DDoS attack mitigations should be part of the organization’s incident response, crisis response and business continuity plans. Having a plan of action in place is critical to ensure a timely recovery from a successful DDoS attack. This plan of action should be practiced and tested regularly to ensure that everything goes as expected and alterations can be made to improve processes and efficiency.
Because successful attacks can have an impact on multiple business units, all stakeholders need to be made aware of the consequences of DDoS attacks and included in the planning process to ensure their interests are properly represented and protected. Typically, an organization's CIO, CSO, CISO, or Risk Management Officer will ultimately be responsible for ensuring this representation happens, and in the event of an attack that significantly impacts multiple business areas, will likely be the one held accountable for the outcome.
The Dell SecureWorks Security and Risk Consulting team can help organizations build an incident response plan that maps to their environment and staffing model. Their expertise and experience in responding to DDoS attacks can provide insight into best practices and common pitfalls. During a typical DDoS Incident Response Plan engagement, the SRC group can help you:
- Understand what your Internet Service Provider is able to do at the provider level
- Understand the limitations of the networking and information systems in your architecture
o Indentify the ‘weakest link’ in the network
o Ensure proper device configurations for identification and mitigation of attacks
o Analyze the cost and benefits of increasing website capacity and resources
o Ensure proper device configurations for identification and mitigation of attacks
o Analyze the cost and benefits of increasing website capacity and resources
- Outline escalation and notification procedures when a DDoS attack is identified
- Record roles and responsibilities during an attack
- Document techniques for identifying the type and source of a DDoS attack
- Record detailed mitigations for various types of attacks - such as implementing strict SYN limits per IP, geographic blocking, or reducing the per-client connection limits at the ASA bundle
- Plan for the public response and communications that will need to occur
- Create an outline for a follow up and lessons learned report
- Additional agreed-upon tasks as requested by the customer
DDoS attacks cannot be prevented, but organizations can become aware of the threat and work proactively to establish countermeasures and incident response plans to mitigate and minimize the potential impact of a determined and well-resourced attacker. Understanding the adversary's tactics, techniques, and procedures, as well as the options available for mitigating the effects, is vital to establishing a strong security posture and planning a rapid, effective response.
A more detailed technical analysis of DDoS attacks is also available, describing the various types of attacks, common tools and tactics, trends in DDoS, countermeasures, and legal issues. The analysis is targeted towards an audience with a solid understanding of networking.
The report is available at: Threat Analysis: Understanding and Combating DDoS Attacks
Should you have any additional questions about how Dell SecureWorks can help your organization plan for or respond to DDoS attacks, contact your account manager, email info@secureworks.com or call (877) 905-6661.
THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES. THE CONTENT IS PROVIDED AS IS, WITHOUT EXPRESS OR IMPLIED WARRANTIES OF ANY KIND.
Download links of Hacking Tools
Hacking Tools
How to be a hacker 101, School in session. ( this post was made first by a member called Bobbreny. Thank you for yout time effort writing this post). I simple edited adding some more material to the post.
Ahhhhh n00bs please speak proper english when asking questions. No leet speaking or "u no wot 1 mean" stuff.
Quite often we get asked to mentor or teach hacking here is your answer:
OK so you’re going to be an Ace #1 hacker. Wanna know
How to get into a system, here is a step by step instruction,
Not only to get into a server but take over the NETWORK, Own it: but the guy that will be tracking you to put your ass in JAIL.
Though you should know who will be after you.
These are the TOP 10 ways into server’s (thanks Riff-raff)
http://msevents.microsoft.com/CUI/E...5&Culture=en-US
(Actually 14 ways into a server) Don't call us for Bail.
But do let us know when you get busted...
O.K. so your not quite up for that yet?
Here are some programs and reading. Contributed by Strader
Here:
Security Links
§ A totally HUGE security archive http://neworder.box.sk/
§ THE best security forums http://www.security-forums.com/
§ Current and archived exploits http://www.securiteam.com/exploits/
§ 'Underground' search engine http://www.warez.com/
§ Default login’s for all sorts of devices http://www.governmentsecurity.org
§ One of the top mainstream security sites http://www.securityfocus.com/
§ TESO Computer security http://teso.scene.at/
§ Asian security group, lots of advisories http://www.shadowpenguin.org/
§ w00w00 Security development http://www.w00w00.org/
§ USSR a strong security group http://www.ussrback.com/
§ Good all around security site http://www.packetstormsecurity.nl
§ Exploits, backdoors, Trojans and more http://www.tlsecurity.net
§ SANS Security Institute with articles on EVERYTHING http://www.sans.org/
§ A Fairly immense WWW security FAQ http://www.w3.org/Security/Faq/
§ Computer Security Encyclopedia http://www.itsecurity.com/
§ Java Security information http://java.sun.com/security/
§ Help Net Security http://www.net-security.org/
§ Security Search Engine http://searchsecurity.techtarget.com/
§ Free BSD security information http://www.freebsd.org/security/
§ Netscape security information http://home.netscape.com/security/
§ Linux security community centre http://www.linuxsecurity.com/
§ Dutch Security Information Network http://www.dsinet.org/
§ Network Security Library http://secinf.net/
§ Infamous happy hacker http://www.happyhacker.org/
§ A once great site from a white hat hacker http://www.antionline.com/
§ Infosec papers and articles http://www.infosecwriters.com/
§ Security/privacy/crypto software archive http://www.wiretapped.net/
§ ISB - Info Sec Bible http://www.securityflaw.com/bible
§ Security tool’s Http://foundstone.com/
http://securitystats.com
Privacy and Anonymity
ÿ All about privacy http://www.privacy.net
ÿ Anonymity, privacy and security http://www.stack.nl/~galactus/remailers/
ÿ Free, anonymous web surfing http://www.anonymizer.com/
ÿ IDSecure service http://www.idzap.com/
ÿ News, information and action http://www.privacy.org/
ÿ Sam Spade Tools http://www.samspade.org/t/
ÿ International PGP homepage http://www.pgpi.org
ÿ Encryptable web-mail http://www.hushmail.com/
ÿ Anonymity software http://www.skuz.net/potatoware/
ÿ REALLY delete your data http://www.cs.auckland.ac.nz/~pgut001/pubs/
ÿ Anonymous access http://www.safeproxy.org/
ÿ Web privacy http://www.rewebber.de/
ÿ A list of web anonymisers http://mikhed.narod.ru/
Cryptography & Encryption
æ All about RSA http://www.rsasecurity.com/
æ Cryptography Archives http://www.kremlinencrypt.com/
æ Cryptography links http://cryptography.org/freecryp.htm
æ Cryptography Info http://world.std.com/~franl/crypto/
æ DriveCrypt http://www.e4m.net/
æ CCIPS http://www.cybercrime.gov/crypto.html
æ Cryptography resource http://www.crypto.com/
æ Bruce Schneier's operation http://www.counterpane.com/
æ Huge Crypto archive http://www.cryptome.org
æ A list of Crypto links http://www.security-forums.com/crypto
Source: http://www.darknet.org.uk/
There could be dead links among those; I got the list from the source above.
The rest of the story
Viruses /Trojans & Firewalls
¿ Trojan archive http://packetstormsecurity.nl/trojans/
¿ Up to date Trojan archive http://www.trojanforge.net/
¿ Fearless, everything Trojan http://www.areyoufearless.com/
¿ A good archive with info on each one http://www.dark-e.com
¿ (I'm a moron)'s official Home Page http://www.(I'm a moron).net/
¿ The BO2k project http://bo2k.sourceforge.net/
¿ Another comprehensive Trojan archive http://www.tlsecurity.net/amt.htm
¿ Home of BackOrifice http://www.cultdeadcow.com/
¿ Huge Trojan removal database http://www.anti-trojan.org/
¿ Excellent Anti-Viral software and Virii Database http://www.sophos.com/
¿ Mcafee's Searchable Virus Information Library http://vil.mcafee.com/
¿ Firewall Guide http://www.firewallguide.com/
Virus Writing
http://vx.netlux.org/lib/static/vdat/tutorial.htm
Nice find Strader...
¿ Firewall FAQ http://www.interhack.net/pubs/fwfaq/
¿ Firewall How To http://www.grennan.com/Firewall-HOWTO.html
¿ Squid http://www.squid-cache.org/
¿ Excellent virus news and info http://www.antivirus-online.de/english/
¿ The ULTIMATE IPTables resource http://www.linuxguruz.org/iptables/
Programming
PHP IDE http://www.phpide.de/
ç Scripts, Source and Books http://www.scriptsearch.com/
ç Java & Internet Glossary http://www.mindprod.com/jgloss.html
ç Java homepage http://java.sun.com/
ç Absolute Java FAQ http://www.javafaq.nu/
ç Thinking in Java http://www.mindview.net/Books/TIJ/
ç JavaScript Resource http://www.javascript.com
ç JavaScripts,tutorials & references http://javascript.internet.com/
ç MySQL home http://www.mysql.com
ç PostgreSQL home http://www.postgresql.org/
ç PHP home page http://www.programmersheaven.com/
ç PHP from hotscripts http://www.hotscripts.com/PHP/
ç PHP resource index http://php.resourceindex.com/
ç PHP FAQ's http://www.faqts.com/
ç PHP Developer resources http://www.phpbuilder.com/
ç Building dynamic sites with PHP http://www.phpwizard.net
ç PHP Developer network http://www.evilwalrus.com/
ç PHP Tutorials and more http://www.thescripts.com/serversidescripting/php
ç PHP Resource list http://www.security-forums.com/forum/php
ç ASPTear http://www.alphasierrapapa.com/IisD...nents/AspTear/
ç ASP Codes and techniques http://www.asptoday.com/
ç ASP, HTML, SQL and more http://www.w3schools.com/
ç Think ASP think... http://www.4guysfromrolla.com/
ç ASP 101 http://www.asp101.com/
ç ASP developers site http://haneng.com/
ç PERL Archive http://www.perlarchive.com/
ç PERL tutorials http://www.perlmonks.org/index.pl?node=Tutorials
ç Old school PERL programming http://www.cgi101.com/
ç Windows programming tools http://www.programmerstools.org/
ç Python homepage http://www.python.org/
ç Object Oriented Programming http://www.oopweb.com/
ç XML 101 http://www.xml101.com
ç Dev-X XML zone http://www.devx.com/xml/
ç Programmers Heaven http://www.programmersheaven.com/
ç Loads of tutorials http://www.echoecho.com
ç Plenty of Web Development scripts http://www.hotscripts.com
ç Code for everything http://www.planet-source-code.com/
ç The definitive Assembly resource http://webster.cs.ucr.edu/ASM
ç C Course http://www.strath.ac.uk/IT/Docs/Ccourse/
ç Another good C course http://www.eskimo.com/~scs/cclass/notes/top.html
'Legal' Hacking
à Zebulun http://www.cyberarmy.com/zebulun/
à Hack me http://loginmatrix.com/hackme/
à Try2Hack http://www.try2hack.nl/
à Hack3r/Roothack http://roothack.org/
à Pull The Plug http://www.pulltheplug.com/
News Groups
A great source of information, discussion and answers to questions
Depending how you put them
ñ alt.hacking.
ñ alt.binaries.hacking.beginner.
ñ alt.computer.security.
ñ alt.security.
ñ alt.os.security.
ñ alt.security.pgp.
ñ alt.security.pgp.patches.
ñ comp.os.linux.security.
ñ comp.os.ms-windows.nt.admin.security.
ñ comp.security.unix.
ñ comp.security.pgp.backdoors.
ñ comp.security.unix.
ñ microsoft.public.security.
ñ microsoft.public.sqlserver.security.
ñ microsoft.public.win2000.security.
tools, google it:
Tools
» THE ultimate port scanner nmap.
» The one and only NT password cracker L0phtcrack.
» Get the latest version of john the ripper.
» Windows process listener Inzider.
» The best packet assembler/analyzer hping.
» Hackers swiss army knife netcat.
» A tool for network monitoring and data acquisition TCPDump.
» The ONLY packet sniffer Ethereal.
» An active reconnaissance network security tool Firewalk.
» Grep your network traffic NGrep.
» NIDS tester from NIDSbench fragrouter.
» The best OS fingerprinter Xprobe.
» Port mapper fport.
» File Integrity checker Tripwire.
» Check for rootkits chkrootkit.
» OSS instrusion detection Snort.
» Security Scanner Nessus.
» TCP/IP Toolkit Paketto.
Nice find Strader........
Hackers Manifesto
http://www.infowar.com/forums/showthread.p...=&threadid=1162
"don't do anything illegal"
Pratice:
http://www.scifi.pages.at/hackits/
(Thanks newbie)
http://www.hackerslab.org/eorg/
(thanks newbie)
http://www.learntohack.org/
(thanks newbie)
http://neworder.box.sk/codebox.links.php?key=36581
(Thanks Net Buster)
http://www.hackthissite.org/
(thanks 55)
Programs applications and other need tools
Browsers
Mozilla Firefox 9.1
http://www.mozilla.org/products/firefox/
Opera
http://www.opera.com/
Netscape 7.1
http://channels.netscape.com/ns/browsers/download.jsp
Anti Virus programs Free
Avast
http://www.avast.com/
AVG
http://www.grisoft.com/us/us_dwnl_free.php
Free antivirus listing page
http://www.freebyte.com/antivirus/
Anti Trojan applications
http://www.emsisoft.com/en/software/free/
Firewalls free
Zone labs
http://www.zonelabs.com/store/conte...reeDownload.jsp
Sygate
http://smb.sygate.com/products/spf_standard.htm
Outpost
http://www.agnitum.com/download/
Kerio
http://www.kerio.com/us/kpf_download.html
Test sites for firewall security
Pcflank
http://www.pcflank.com/
Gibson Research Corporation
http://www.grc.com/default.htm
Misc. sites that have been posted over the years
How to read NETSTAT –an
http://www.geocities.com/merijn_bel.../netstatan.html
Dshield Distributed Intrusion Detection System
http://www.dshield.org/index.php
Hackers watch
http://www.hackerwatch.org/
TCP/ IP Ports list
http://www.chebucto.ns.ca/~rakerman/port-table.html
Network Tools
http://lists.gpick.com/pages/Network_Tools.htm
Hacking text files (older stuff but still useful )\
http://www.textfiles.com/hacking/INTERNET/
Beta News
http://www.betanews.com/
GIF works
http://www.gifworks.com/
Secunia Security pages virus alerts and such
http://secunia.com/ multiple_browse...ty_te
st/
Anti spyware apps
Spyware blaster
http://www.javacoolsoftware.com/
Spybot S&D
http://www.pcworld.com/downloads/fi...id,22262,00.asp
Spyware guard
http://www.javacoolsoftware.com/spywareguard.html
Adware
http://www.lavasoftusa.com/software/adaware/
Here are some tools posted by my friend Splabster(thank you for taking the time typing those tools) :
General System & Network Probing:
Sam Spade http://www.samspade.org/ssw
Online tools http://www.network-tools.com
Online tool http://visualroute.visualware.com
Online tool http://www.norid.no/domenenavnbaser/domreg-alpha.html
Nmap http://www.nmap.org
Scanline http://www.foundstone.com
SuperScan http://www.foundstone.com
Icmpenum http://razor.bindview.com/tools/des...num_readme.html
Snscan http://www.foundstone.com
Ethereal http://www.ethereal.com
Ettercap http://ettercap.sourceforge.net
Xprobe2 http://www.sys-security.com/html/projects/X.html
Hping2 http://www.hping.org/
SQLping http://www.sqlsecurity.com/scripts.asp
Amap http://www.thc.org/releases.php
Tcp Traceroute http://michael.toren.net/code/tcptraceroute
VisualRoute http://www.visualware.com/visualroute/index.html
Enumerating & Compromising Windows
Netcat http://www.atstake.com/research/tools/index.html
Zebedee http://www.winton.org.uk/sebedee/
Desproxy http://desproxy.courceforge.net/
Winfo http://ntsecurity.nu/toolbox/winfo
enum http://razor.bindview.com/tools/des...num_readme.html
Ldp LDAP query tool available in the windows 2000 server cd-rom
DumpSec http://www.somarsoft.com/
Userdump http://www.hammerofgod.com/download.htm
NTFSdos http://www.sysinternals.com/ntw2k/freeware/NTFDOS.shtml
Chntpw http://home.eunet.no/~pnordahl/ntpasswd/
PWDump3 http://www.polivec.com/pwdump3.html
Lsadump2 http://razor.bindview.com/tools/index.shtml
PipeUpAdmin http://content.443.ch/pub/security/...peup/W2KPipeUp/
Psexec http://www.sysinternals.com/ntw2k/freeware/psexec.shtml
Ettercap address above
Brutus http://www.hoobie.net/brutus/index.html
Hydra http://www.thc.org/releases.php
John http://www.openwall.com/john
VNCcrack http://www.phenoelit.de/fr/tools.html
Cain & Abel http://www.oxid.it/projects.html
ClearLogs http://www.ntsecurity.nu/toolbox/
WinZapper http://www.ntsecurity.nu/toolbox/
SQLdict http://www.ntsecurity.nu/toolbox/sqldict
Enumerating & Compromising UNIX
Netcat
Zebedee
Desproxy
Ettercap
Xscan http://packetstormsecurity.nl/Exploit_Code_Archive/
Xwhatchwin http://www.deter.com/unix/software/xwatchwin.tgz
Xkey http://www.deter.com/unix/software/xkey.c
Xspy http://www.deter.com/unix/software/xspy-1.0c.tgz
YPX http://www.deter.com/unix/software/ypx.sh.gz
Hunt http://lin.fsid.cvut.cz/~kra/index.html#HUNT
John
Brutus
Hydra
VNCcrack
SQLdict
Zap3 http://packetstormsecurity.nl/UNIX/...ion/log-wipers/
Enumerating & Compromising Novell
Pandora http://www.nmrc.org/project/pandora/index.html
On-site Admin http://www.environmental-center.com/freeware/onsite.htm
NCPQuery http://razor.bindview.com/tools/index.shtml
Enumerating & Compromising Wireless
Netstumbler http://www.netstumbler.com
Kismet http://www.kismetwireless.net/download.shtml
kisMac (for mac users) http://www.binaervarianz.de/projekt...ac/download.php
Airsnort http://airsnort.shmoo.com/
Airtraf http://www.elixar.com/index.html
SMAC http://www.klcconsulting.net/smac
Accessories http://www.fab-corp.com
General System & Network Vulnerability Checking
Nessus http://www.nessus.org
SARA http://www-arc.com/products.shtml
Nikto http://www.cirt.net/code/nikto.shtml
System Forensics Tools
Vision http://www.foundstone.com/knowledge...esc/vision.html
ListDLLs http://www.sysinternals.com/ntw2k/f.../listdlls.shtml
Process Explorer http://www.sysinternals.com/ntw2k/f...e/procexp.shtml
Coroner's Toolkit http://porcupine.org/forensics/tct.html
LADS http://www.sysinternals.com/ntw2k/f.../listdlls.shtml
Chkrootkit http://www.chkrootkit.org/
WinHex http://www.winhex.com/winhex/index-m.html
Active @ Undelete http://www.active-undelete.com/
Web Hacking tools
Black Widow http://www.softbytelabs.com/Frames.html
Web Sleuth http://sandsprite.com/Sleuth
Wfetch http://support.microsoft.com/defaul...B;en-us;q284285
Tsql http://www.aspalliance.com/mtgal/source_code/tsql.exe
Spike Proxy http://www.immunitysec.com/spike.html
Remote Command Shell/Remote Access Trojans/Rootkits
(I'm a moron) Trojan http://(I'm a moron).net/
Barok active Trojan http://www.thenewbiesarea.com/trojans.shtml
AckCmd backdoor http://ntsecurity.ni/toolbox/
Tini backdoor http://ntsecurity.ni/toolbox/
Psexec r-shell http://www.sysinternals.com/ntw2k/freeware/psexec.shtml
Rwwwshell r-shell http://www.thc.org/releases/rwwwshell-2.0.pl.gz
LRK5 rootkit http://www.hackersplayground.org/tools.html
Knark 2.4 rootkit http://www.hackersplayground.org/tools.html
Miscellaneous Tools
Fragrouter http://packetstorm.widexs.nl/UNIX/I.../nidsbench.html
Stunnel http://www.stunnel.org
WinRelay http://www.ntsecurity.nu/toolbox/
Fpipe http://www.foundstone.com/resources/freetools.htm
Tight VNC http://www.tightvnc.com
FileGateway http://www.steelbytes.com
Remote Anything http://remote-anything.com/en/ra_index.htm
TinyWeb http://www.ritlabs.com/tinyweb/index.html
IKS 200 key logger http://www.amecisco.com/index.htm
KLogger http://www.ntsecurity.nu/toolbox/
ShowWin http://www.foundstone.com/knowledge/free_tools.html
KEYhatcher http://www.keykatcher.com/howit.htm
Hex Editors http://www.expertcomsoft.com
http://www.winhex.com/winhex/index-m.html
Secure hard disk wiping and deletion
http://www.heidi.ie
http://www.jetico.com
http://www.winhex.com/winhex/index-m.html
Trinux http://trinux.sourceforge.net/
Silk Rope 2K http://www.hackersplayground.org/tools.html
CMOS killer http://www.hackersplayground.org/tools.html
LDAP Browser http://www.softerra.com/products/ldabrowser.php
QTODBC http://gpoulose.home.att.net/Tools/QTADO40_sr.exe
Host Lockdown/Protection/Assessment Tools
Bastille http://www.bastille-linux.org
lpchains http://www.linuxplanet.com/linuxpla...torials/2100/3/
Apache Shell http://ftp.porcupine.org/pub/security/index.html
Titan http://www.fish.com/titan
Tara http://www-arc.com/products.shtml
Tcpwrappers http://www.linuxsecurity.com/docs/colsfaq.html#4.5
URLscan http://www.microsoft.com/technet/security/tools/
IISLockdown http://www.microsoft.com/technet/security/tools/
Tripwire http://www.tripwire.com/
HFNETchk http://www.microsoft.com/technet/security/tools/
MS SQL Lockdown Script http://www.sqlsecurity.com/DesktopD...ndex=4&tabid=12
UNIX/Windows/router assessment tools http://www.cisecurity.org/
Secure Cisco Router Template http://www.cymru.com/Documents/secure-ios-template.html
Secure Cisco Switch Template
http://www.qorbit.net/documents/cat...re-template.pdf
Snort http://www.snort.org
Swatch http://swatch.sourceforge.net
Secure Remote Password http://srp.stanford.edu/
Software Code Review links https://sardonix.org/auditing_Resources.html
Sawmill http://www.sawmill.net/features.html
courtesy : criticalsecurity
How to be a hacker 101, School in session. ( this post was made first by a member called Bobbreny. Thank you for yout time effort writing this post). I simple edited adding some more material to the post.
Ahhhhh n00bs please speak proper english when asking questions. No leet speaking or "u no wot 1 mean" stuff.
Quite often we get asked to mentor or teach hacking here is your answer:
OK so you’re going to be an Ace #1 hacker. Wanna know
How to get into a system, here is a step by step instruction,
Not only to get into a server but take over the NETWORK, Own it: but the guy that will be tracking you to put your ass in JAIL.
Though you should know who will be after you.
These are the TOP 10 ways into server’s (thanks Riff-raff)
http://msevents.microsoft.com/CUI/E...5&Culture=en-US
(Actually 14 ways into a server) Don't call us for Bail.
But do let us know when you get busted...
O.K. so your not quite up for that yet?
Here are some programs and reading. Contributed by Strader
Here:
Security Links
§ A totally HUGE security archive http://neworder.box.sk/
§ THE best security forums http://www.security-forums.com/
§ Current and archived exploits http://www.securiteam.com/exploits/
§ 'Underground' search engine http://www.warez.com/
§ Default login’s for all sorts of devices http://www.governmentsecurity.org
§ One of the top mainstream security sites http://www.securityfocus.com/
§ TESO Computer security http://teso.scene.at/
§ Asian security group, lots of advisories http://www.shadowpenguin.org/
§ w00w00 Security development http://www.w00w00.org/
§ USSR a strong security group http://www.ussrback.com/
§ Good all around security site http://www.packetstormsecurity.nl
§ Exploits, backdoors, Trojans and more http://www.tlsecurity.net
§ SANS Security Institute with articles on EVERYTHING http://www.sans.org/
§ A Fairly immense WWW security FAQ http://www.w3.org/Security/Faq/
§ Computer Security Encyclopedia http://www.itsecurity.com/
§ Java Security information http://java.sun.com/security/
§ Help Net Security http://www.net-security.org/
§ Security Search Engine http://searchsecurity.techtarget.com/
§ Free BSD security information http://www.freebsd.org/security/
§ Netscape security information http://home.netscape.com/security/
§ Linux security community centre http://www.linuxsecurity.com/
§ Dutch Security Information Network http://www.dsinet.org/
§ Network Security Library http://secinf.net/
§ Infamous happy hacker http://www.happyhacker.org/
§ A once great site from a white hat hacker http://www.antionline.com/
§ Infosec papers and articles http://www.infosecwriters.com/
§ Security/privacy/crypto software archive http://www.wiretapped.net/
§ ISB - Info Sec Bible http://www.securityflaw.com/bible
§ Security tool’s Http://foundstone.com/
http://securitystats.com
Privacy and Anonymity
ÿ All about privacy http://www.privacy.net
ÿ Anonymity, privacy and security http://www.stack.nl/~galactus/remailers/
ÿ Free, anonymous web surfing http://www.anonymizer.com/
ÿ IDSecure service http://www.idzap.com/
ÿ News, information and action http://www.privacy.org/
ÿ Sam Spade Tools http://www.samspade.org/t/
ÿ International PGP homepage http://www.pgpi.org
ÿ Encryptable web-mail http://www.hushmail.com/
ÿ Anonymity software http://www.skuz.net/potatoware/
ÿ REALLY delete your data http://www.cs.auckland.ac.nz/~pgut001/pubs/
ÿ Anonymous access http://www.safeproxy.org/
ÿ Web privacy http://www.rewebber.de/
ÿ A list of web anonymisers http://mikhed.narod.ru/
Cryptography & Encryption
æ All about RSA http://www.rsasecurity.com/
æ Cryptography Archives http://www.kremlinencrypt.com/
æ Cryptography links http://cryptography.org/freecryp.htm
æ Cryptography Info http://world.std.com/~franl/crypto/
æ DriveCrypt http://www.e4m.net/
æ CCIPS http://www.cybercrime.gov/crypto.html
æ Cryptography resource http://www.crypto.com/
æ Bruce Schneier's operation http://www.counterpane.com/
æ Huge Crypto archive http://www.cryptome.org
æ A list of Crypto links http://www.security-forums.com/crypto
Source: http://www.darknet.org.uk/
There could be dead links among those; I got the list from the source above.
The rest of the story
Viruses /Trojans & Firewalls
¿ Trojan archive http://packetstormsecurity.nl/trojans/
¿ Up to date Trojan archive http://www.trojanforge.net/
¿ Fearless, everything Trojan http://www.areyoufearless.com/
¿ A good archive with info on each one http://www.dark-e.com
¿ (I'm a moron)'s official Home Page http://www.(I'm a moron).net/
¿ The BO2k project http://bo2k.sourceforge.net/
¿ Another comprehensive Trojan archive http://www.tlsecurity.net/amt.htm
¿ Home of BackOrifice http://www.cultdeadcow.com/
¿ Huge Trojan removal database http://www.anti-trojan.org/
¿ Excellent Anti-Viral software and Virii Database http://www.sophos.com/
¿ Mcafee's Searchable Virus Information Library http://vil.mcafee.com/
¿ Firewall Guide http://www.firewallguide.com/
Virus Writing
http://vx.netlux.org/lib/static/vdat/tutorial.htm
Nice find Strader...
¿ Firewall FAQ http://www.interhack.net/pubs/fwfaq/
¿ Firewall How To http://www.grennan.com/Firewall-HOWTO.html
¿ Squid http://www.squid-cache.org/
¿ Excellent virus news and info http://www.antivirus-online.de/english/
¿ The ULTIMATE IPTables resource http://www.linuxguruz.org/iptables/
Programming
PHP IDE http://www.phpide.de/
ç Scripts, Source and Books http://www.scriptsearch.com/
ç Java & Internet Glossary http://www.mindprod.com/jgloss.html
ç Java homepage http://java.sun.com/
ç Absolute Java FAQ http://www.javafaq.nu/
ç Thinking in Java http://www.mindview.net/Books/TIJ/
ç JavaScript Resource http://www.javascript.com
ç JavaScripts,tutorials & references http://javascript.internet.com/
ç MySQL home http://www.mysql.com
ç PostgreSQL home http://www.postgresql.org/
ç PHP home page http://www.programmersheaven.com/
ç PHP from hotscripts http://www.hotscripts.com/PHP/
ç PHP resource index http://php.resourceindex.com/
ç PHP FAQ's http://www.faqts.com/
ç PHP Developer resources http://www.phpbuilder.com/
ç Building dynamic sites with PHP http://www.phpwizard.net
ç PHP Developer network http://www.evilwalrus.com/
ç PHP Tutorials and more http://www.thescripts.com/serversidescripting/php
ç PHP Resource list http://www.security-forums.com/forum/php
ç ASPTear http://www.alphasierrapapa.com/IisD...nents/AspTear/
ç ASP Codes and techniques http://www.asptoday.com/
ç ASP, HTML, SQL and more http://www.w3schools.com/
ç Think ASP think... http://www.4guysfromrolla.com/
ç ASP 101 http://www.asp101.com/
ç ASP developers site http://haneng.com/
ç PERL Archive http://www.perlarchive.com/
ç PERL tutorials http://www.perlmonks.org/index.pl?node=Tutorials
ç Old school PERL programming http://www.cgi101.com/
ç Windows programming tools http://www.programmerstools.org/
ç Python homepage http://www.python.org/
ç Object Oriented Programming http://www.oopweb.com/
ç XML 101 http://www.xml101.com
ç Dev-X XML zone http://www.devx.com/xml/
ç Programmers Heaven http://www.programmersheaven.com/
ç Loads of tutorials http://www.echoecho.com
ç Plenty of Web Development scripts http://www.hotscripts.com
ç Code for everything http://www.planet-source-code.com/
ç The definitive Assembly resource http://webster.cs.ucr.edu/ASM
ç C Course http://www.strath.ac.uk/IT/Docs/Ccourse/
ç Another good C course http://www.eskimo.com/~scs/cclass/notes/top.html
'Legal' Hacking
à Zebulun http://www.cyberarmy.com/zebulun/
à Hack me http://loginmatrix.com/hackme/
à Try2Hack http://www.try2hack.nl/
à Hack3r/Roothack http://roothack.org/
à Pull The Plug http://www.pulltheplug.com/
News Groups
A great source of information, discussion and answers to questions
Depending how you put them
ñ alt.hacking.
ñ alt.binaries.hacking.beginner.
ñ alt.computer.security.
ñ alt.security.
ñ alt.os.security.
ñ alt.security.pgp.
ñ alt.security.pgp.patches.
ñ comp.os.linux.security.
ñ comp.os.ms-windows.nt.admin.security.
ñ comp.security.unix.
ñ comp.security.pgp.backdoors.
ñ comp.security.unix.
ñ microsoft.public.security.
ñ microsoft.public.sqlserver.security.
ñ microsoft.public.win2000.security.
tools, google it:
Tools
» THE ultimate port scanner nmap.
» The one and only NT password cracker L0phtcrack.
» Get the latest version of john the ripper.
» Windows process listener Inzider.
» The best packet assembler/analyzer hping.
» Hackers swiss army knife netcat.
» A tool for network monitoring and data acquisition TCPDump.
» The ONLY packet sniffer Ethereal.
» An active reconnaissance network security tool Firewalk.
» Grep your network traffic NGrep.
» NIDS tester from NIDSbench fragrouter.
» The best OS fingerprinter Xprobe.
» Port mapper fport.
» File Integrity checker Tripwire.
» Check for rootkits chkrootkit.
» OSS instrusion detection Snort.
» Security Scanner Nessus.
» TCP/IP Toolkit Paketto.
Nice find Strader........
Hackers Manifesto
http://www.infowar.com/forums/showthread.p...=&threadid=1162
"don't do anything illegal"
Pratice:
http://www.scifi.pages.at/hackits/
(Thanks newbie)
http://www.hackerslab.org/eorg/
(thanks newbie)
http://www.learntohack.org/
(thanks newbie)
http://neworder.box.sk/codebox.links.php?key=36581
(Thanks Net Buster)
http://www.hackthissite.org/
(thanks 55)
Programs applications and other need tools
Browsers
Mozilla Firefox 9.1
http://www.mozilla.org/products/firefox/
Opera
http://www.opera.com/
Netscape 7.1
http://channels.netscape.com/ns/browsers/download.jsp
Anti Virus programs Free
Avast
http://www.avast.com/
AVG
http://www.grisoft.com/us/us_dwnl_free.php
Free antivirus listing page
http://www.freebyte.com/antivirus/
Anti Trojan applications
http://www.emsisoft.com/en/software/free/
Firewalls free
Zone labs
http://www.zonelabs.com/store/conte...reeDownload.jsp
Sygate
http://smb.sygate.com/products/spf_standard.htm
Outpost
http://www.agnitum.com/download/
Kerio
http://www.kerio.com/us/kpf_download.html
Test sites for firewall security
Pcflank
http://www.pcflank.com/
Gibson Research Corporation
http://www.grc.com/default.htm
Misc. sites that have been posted over the years
How to read NETSTAT –an
http://www.geocities.com/merijn_bel.../netstatan.html
Dshield Distributed Intrusion Detection System
http://www.dshield.org/index.php
Hackers watch
http://www.hackerwatch.org/
TCP/ IP Ports list
http://www.chebucto.ns.ca/~rakerman/port-table.html
Network Tools
http://lists.gpick.com/pages/Network_Tools.htm
Hacking text files (older stuff but still useful )\
http://www.textfiles.com/hacking/INTERNET/
Beta News
http://www.betanews.com/
GIF works
http://www.gifworks.com/
Secunia Security pages virus alerts and such
http://secunia.com/ multiple_browse...ty_te
st/
Anti spyware apps
Spyware blaster
http://www.javacoolsoftware.com/
Spybot S&D
http://www.pcworld.com/downloads/fi...id,22262,00.asp
Spyware guard
http://www.javacoolsoftware.com/spywareguard.html
Adware
http://www.lavasoftusa.com/software/adaware/
Here are some tools posted by my friend Splabster(thank you for taking the time typing those tools) :
General System & Network Probing:
Sam Spade http://www.samspade.org/ssw
Online tools http://www.network-tools.com
Online tool http://visualroute.visualware.com
Online tool http://www.norid.no/domenenavnbaser/domreg-alpha.html
Nmap http://www.nmap.org
Scanline http://www.foundstone.com
SuperScan http://www.foundstone.com
Icmpenum http://razor.bindview.com/tools/des...num_readme.html
Snscan http://www.foundstone.com
Ethereal http://www.ethereal.com
Ettercap http://ettercap.sourceforge.net
Xprobe2 http://www.sys-security.com/html/projects/X.html
Hping2 http://www.hping.org/
SQLping http://www.sqlsecurity.com/scripts.asp
Amap http://www.thc.org/releases.php
Tcp Traceroute http://michael.toren.net/code/tcptraceroute
VisualRoute http://www.visualware.com/visualroute/index.html
Enumerating & Compromising Windows
Netcat http://www.atstake.com/research/tools/index.html
Zebedee http://www.winton.org.uk/sebedee/
Desproxy http://desproxy.courceforge.net/
Winfo http://ntsecurity.nu/toolbox/winfo
enum http://razor.bindview.com/tools/des...num_readme.html
Ldp LDAP query tool available in the windows 2000 server cd-rom
DumpSec http://www.somarsoft.com/
Userdump http://www.hammerofgod.com/download.htm
NTFSdos http://www.sysinternals.com/ntw2k/freeware/NTFDOS.shtml
Chntpw http://home.eunet.no/~pnordahl/ntpasswd/
PWDump3 http://www.polivec.com/pwdump3.html
Lsadump2 http://razor.bindview.com/tools/index.shtml
PipeUpAdmin http://content.443.ch/pub/security/...peup/W2KPipeUp/
Psexec http://www.sysinternals.com/ntw2k/freeware/psexec.shtml
Ettercap address above
Brutus http://www.hoobie.net/brutus/index.html
Hydra http://www.thc.org/releases.php
John http://www.openwall.com/john
VNCcrack http://www.phenoelit.de/fr/tools.html
Cain & Abel http://www.oxid.it/projects.html
ClearLogs http://www.ntsecurity.nu/toolbox/
WinZapper http://www.ntsecurity.nu/toolbox/
SQLdict http://www.ntsecurity.nu/toolbox/sqldict
Enumerating & Compromising UNIX
Netcat
Zebedee
Desproxy
Ettercap
Xscan http://packetstormsecurity.nl/Exploit_Code_Archive/
Xwhatchwin http://www.deter.com/unix/software/xwatchwin.tgz
Xkey http://www.deter.com/unix/software/xkey.c
Xspy http://www.deter.com/unix/software/xspy-1.0c.tgz
YPX http://www.deter.com/unix/software/ypx.sh.gz
Hunt http://lin.fsid.cvut.cz/~kra/index.html#HUNT
John
Brutus
Hydra
VNCcrack
SQLdict
Zap3 http://packetstormsecurity.nl/UNIX/...ion/log-wipers/
Enumerating & Compromising Novell
Pandora http://www.nmrc.org/project/pandora/index.html
On-site Admin http://www.environmental-center.com/freeware/onsite.htm
NCPQuery http://razor.bindview.com/tools/index.shtml
Enumerating & Compromising Wireless
Netstumbler http://www.netstumbler.com
Kismet http://www.kismetwireless.net/download.shtml
kisMac (for mac users) http://www.binaervarianz.de/projekt...ac/download.php
Airsnort http://airsnort.shmoo.com/
Airtraf http://www.elixar.com/index.html
SMAC http://www.klcconsulting.net/smac
Accessories http://www.fab-corp.com
General System & Network Vulnerability Checking
Nessus http://www.nessus.org
SARA http://www-arc.com/products.shtml
Nikto http://www.cirt.net/code/nikto.shtml
System Forensics Tools
Vision http://www.foundstone.com/knowledge...esc/vision.html
ListDLLs http://www.sysinternals.com/ntw2k/f.../listdlls.shtml
Process Explorer http://www.sysinternals.com/ntw2k/f...e/procexp.shtml
Coroner's Toolkit http://porcupine.org/forensics/tct.html
LADS http://www.sysinternals.com/ntw2k/f.../listdlls.shtml
Chkrootkit http://www.chkrootkit.org/
WinHex http://www.winhex.com/winhex/index-m.html
Active @ Undelete http://www.active-undelete.com/
Web Hacking tools
Black Widow http://www.softbytelabs.com/Frames.html
Web Sleuth http://sandsprite.com/Sleuth
Wfetch http://support.microsoft.com/defaul...B;en-us;q284285
Tsql http://www.aspalliance.com/mtgal/source_code/tsql.exe
Spike Proxy http://www.immunitysec.com/spike.html
Remote Command Shell/Remote Access Trojans/Rootkits
(I'm a moron) Trojan http://(I'm a moron).net/
Barok active Trojan http://www.thenewbiesarea.com/trojans.shtml
AckCmd backdoor http://ntsecurity.ni/toolbox/
Tini backdoor http://ntsecurity.ni/toolbox/
Psexec r-shell http://www.sysinternals.com/ntw2k/freeware/psexec.shtml
Rwwwshell r-shell http://www.thc.org/releases/rwwwshell-2.0.pl.gz
LRK5 rootkit http://www.hackersplayground.org/tools.html
Knark 2.4 rootkit http://www.hackersplayground.org/tools.html
Miscellaneous Tools
Fragrouter http://packetstorm.widexs.nl/UNIX/I.../nidsbench.html
Stunnel http://www.stunnel.org
WinRelay http://www.ntsecurity.nu/toolbox/
Fpipe http://www.foundstone.com/resources/freetools.htm
Tight VNC http://www.tightvnc.com
FileGateway http://www.steelbytes.com
Remote Anything http://remote-anything.com/en/ra_index.htm
TinyWeb http://www.ritlabs.com/tinyweb/index.html
IKS 200 key logger http://www.amecisco.com/index.htm
KLogger http://www.ntsecurity.nu/toolbox/
ShowWin http://www.foundstone.com/knowledge/free_tools.html
KEYhatcher http://www.keykatcher.com/howit.htm
Hex Editors http://www.expertcomsoft.com
http://www.winhex.com/winhex/index-m.html
Secure hard disk wiping and deletion
http://www.heidi.ie
http://www.jetico.com
http://www.winhex.com/winhex/index-m.html
Trinux http://trinux.sourceforge.net/
Silk Rope 2K http://www.hackersplayground.org/tools.html
CMOS killer http://www.hackersplayground.org/tools.html
LDAP Browser http://www.softerra.com/products/ldabrowser.php
QTODBC http://gpoulose.home.att.net/Tools/QTADO40_sr.exe
Host Lockdown/Protection/Assessment Tools
Bastille http://www.bastille-linux.org
lpchains http://www.linuxplanet.com/linuxpla...torials/2100/3/
Apache Shell http://ftp.porcupine.org/pub/security/index.html
Titan http://www.fish.com/titan
Tara http://www-arc.com/products.shtml
Tcpwrappers http://www.linuxsecurity.com/docs/colsfaq.html#4.5
URLscan http://www.microsoft.com/technet/security/tools/
IISLockdown http://www.microsoft.com/technet/security/tools/
Tripwire http://www.tripwire.com/
HFNETchk http://www.microsoft.com/technet/security/tools/
MS SQL Lockdown Script http://www.sqlsecurity.com/DesktopD...ndex=4&tabid=12
UNIX/Windows/router assessment tools http://www.cisecurity.org/
Secure Cisco Router Template http://www.cymru.com/Documents/secure-ios-template.html
Secure Cisco Switch Template
http://www.qorbit.net/documents/cat...re-template.pdf
Snort http://www.snort.org
Swatch http://swatch.sourceforge.net
Secure Remote Password http://srp.stanford.edu/
Software Code Review links https://sardonix.org/auditing_Resources.html
Sawmill http://www.sawmill.net/features.html
courtesy : criticalsecurity
Remote 60 Professional - Control Your Phone from PC
Remote 60 Professional - Control Your Phone from PC
NEW: Now also running on Nokia N70, 668x, 6630, 6670, 3230, 6260 and 7610
NEW: Connect via USB with the DKU-2 cable (compatible phones only)
NEW: High performance screen algorithm using pure ARM/Thumb assembler and new compression scheme
Remote S60 Professional - Operate your phone from your desktop PC

 Remote S60 Professional by mobileways.de lets you operate your Series 60 phone from your Windows computer. You can access and control all applications on your phone by using your PC's keyboard while watching the screen of your phone in a virtual window in real time.
Remote S60 Professional by mobileways.de lets you operate your Series 60 phone from your Windows computer. You can access and control all applications on your phone by using your PC's keyboard while watching the screen of your phone in a virtual window in real time.
The Perfect Tool for Presentations, Tutorials or Device and Application Testing
With Remote S60 Professional, you can conveniently demo any applications or services on your phone in realtime. Remote S60 Professional displays your phone's screen in a virtual window on your PC. You can either use a wireless bluetooth connection for best mobility during your presentation or a USB cable (DKU-2) for best realtime performance.
Remote S60 Professional supports skins for different mobile phone models, offers a customizable (HTML) fullscreen mode and allows you to record AVI movies.
For device and service testing, just let your automated testing tool control the Remote S60 Professional Windows application. You can connect multiple devices to one PC by using multiple instances of Remote S60 Professional.
Manage your Everyday Tasks
Remote S60 Professional helps you compose SMS, enter contacts, add WAP/WEB URLs, create and change calender entries or manage your phone's settings with ease.
Features of Remote S60 Professional:
* Connect your phone with the USB cable DKU-2 (compatible Series 60 v2 phones only!) or by Bluetooth Serial Port
* For (old) Series 60 v1 phones: conveniently connect via the PC Suite / mRouter (Nokia 6600, 3650, N-Gage, Siemens SX1, Sendo X, Panasonic X700/X800)
* Support for multiple skins (showing different mobile phone models)
* Customizable (HTML) fullscreen mode (with zoom feature)
* 3 different zoom levels (2x, 3x and 4x)
* Use your keyboard to control your phone in realtime
* Make screenshots, copy them to the clipboard or save them to your PC
* Create AVI movies while navigating on your phone
* Profiles for quickly switching between different performance settings
* Advanced options for balancing performance vs. power consumption:
Reduced color modes, different compression levels, application priority, sampling frequency
* Multiple devices connected to the same PC by using multiple instances of Remote S60 Professional
You need to install two softwares for that..
Download:
1st Software(Remote S60 Professional)
2nd Software(Softcam)
NEW: Now also running on Nokia N70, 668x, 6630, 6670, 3230, 6260 and 7610
NEW: Connect via USB with the DKU-2 cable (compatible phones only)
NEW: High performance screen algorithm using pure ARM/Thumb assembler and new compression scheme
Remote S60 Professional - Operate your phone from your desktop PC

 Remote S60 Professional by mobileways.de lets you operate your Series 60 phone from your Windows computer. You can access and control all applications on your phone by using your PC's keyboard while watching the screen of your phone in a virtual window in real time.
Remote S60 Professional by mobileways.de lets you operate your Series 60 phone from your Windows computer. You can access and control all applications on your phone by using your PC's keyboard while watching the screen of your phone in a virtual window in real time.The Perfect Tool for Presentations, Tutorials or Device and Application Testing
With Remote S60 Professional, you can conveniently demo any applications or services on your phone in realtime. Remote S60 Professional displays your phone's screen in a virtual window on your PC. You can either use a wireless bluetooth connection for best mobility during your presentation or a USB cable (DKU-2) for best realtime performance.
Remote S60 Professional supports skins for different mobile phone models, offers a customizable (HTML) fullscreen mode and allows you to record AVI movies.
For device and service testing, just let your automated testing tool control the Remote S60 Professional Windows application. You can connect multiple devices to one PC by using multiple instances of Remote S60 Professional.
Manage your Everyday Tasks
Remote S60 Professional helps you compose SMS, enter contacts, add WAP/WEB URLs, create and change calender entries or manage your phone's settings with ease.
Features of Remote S60 Professional:
* Connect your phone with the USB cable DKU-2 (compatible Series 60 v2 phones only!) or by Bluetooth Serial Port
* For (old) Series 60 v1 phones: conveniently connect via the PC Suite / mRouter (Nokia 6600, 3650, N-Gage, Siemens SX1, Sendo X, Panasonic X700/X800)
* Support for multiple skins (showing different mobile phone models)
* Customizable (HTML) fullscreen mode (with zoom feature)
* 3 different zoom levels (2x, 3x and 4x)
* Use your keyboard to control your phone in realtime
* Make screenshots, copy them to the clipboard or save them to your PC
* Create AVI movies while navigating on your phone
* Profiles for quickly switching between different performance settings
* Advanced options for balancing performance vs. power consumption:
Reduced color modes, different compression levels, application priority, sampling frequency
* Multiple devices connected to the same PC by using multiple instances of Remote S60 Professional
You need to install two softwares for that..
Download:
1st Software(Remote S60 Professional)
2nd Software(Softcam)
Hacking Web Servers: A Step by Step Beginner Guide
I am asked at least 5 or more times a day by young, beginning "hackers", "How can I hack?" or "Is there a way to hack a web site?"
Well there is. There are, in fact, literally hundreds of ways to do this. I will discuss a few in this text to get you started. Every hacker has to start somehow and hacking web servers and ftp servers is one of the easiest ways.If you are reading this I am assuming that you already have a basic knowledge of how web servers work and how to use some form of UNIX. But I am going to
explain that stuff anyway for those of you who don't know.
Part 1: Simple UNIX Commands
Most DOS commands have UNIX and Linux equivalents. Listed below are
some of the main commands you will need to know to use a shell account.
Part 2: Cracking Passwords
On UNIX systems the file that contains the passwords for all the users on the system is located in the /etc directory. The filename is passwd. I bet your thinking....
"Great. All I have to do is get the file called /etc/passwd and I'll be a hacker."
If that is what you are thinking then you are dead wrong. All the accounts in the passwd file have encrypted passwords. Thesepasswords are one-way encrypted which means that there is no way to decrypt them. However, there are programs that can be used to obtain passwords from the file. The name of the program that I have found to be the best password cracker is called "Cracker Jack" This program uses a dictionary file composedof thousands of words. It compares the encrypted forms of the words in the list to the encrypted passwords in the passwd file and it notifies you when it finds a match.However you can use others like “Cain and Abel” or “John The Ripper (JTR)”
Part 3: The Hard Part (Finding Password Files)
Up till now I have been telling you the easy parts of hacking a
server. Now we get to the more difficult part. It's common sense. If the system administrator has a file that has passwords for everyone on his or her system they are not going to just give it to you. You have to have a way to retrieve the “/etc/passwd” file without logging into the system. There are 2 simple ways that this can sometimes be accomplished. Often the “/etc directory” is not blocked from FTP. To get the passwd file this way try using an FTP client to access the site anonymously then check the “/etc” directory to see if access to the passwd file is restricted. If it is not restricted then download the file and run Cracker Jack on it. If it is restricted then try plan B. On some systems there is a file called PHF in the “/cgi-bin” directory. If there is then you are in luck. PHF allows users to gain remote access to files (including the “/etc/passwd” file) over the world wide web. To try this method goto your web browser and type in this URL:
For example, if I wanted to hack St. Louis University (and I have already) Iwould type in
Here's a hint: try www.spawn.com and www.garply.com
If the preceding to methods fail then try any way you can think of to get that file. If you do get the file and all the items in the second field are X or ! or * then the password file is shadowed. Shadowing is just a method of adding extra security to prevent hackers and other unwanted people from using the password file. Unfortunately there is no way to "unshadow" a password file
but sometimes there are backup password files that aren't shadowed. Try looking for files such as “/etc/shadow” and other stuff like that.
Part 4: Logging In To "Your" New Shell
OK....This is where you use what you found using Cracker Jack.
Usernames and passwords. Run your telnet client and telent to the server that you cracked the passwords for, such as www.slu.edu. When you are connected it will give a login screen that asks for a login names and password and usually information on the operating system that the server is using (usually UNIX,
linux, aix, irix, ultrix, bsd, or sometimes even DOS or Vax / Vms). Just type in the information you got after cracking the passwd file and whatever you know about UNIX to do whatever you feel like doing. But remember that
If you feel that you have what it takes to be a serious hacker then you must first know a clear definition of hacking and how to be an ethical hacker. Become familiar with Unix environments and if you are only just starting to learn to hack, visit a local library and find some books on various operating systems on the Internet and how they work. Or you could go to a book store and buy a couple Internet security books (They often explain how hackers penetrate systems and that is something a beginner could use as an advantage.),Join forums,read Ebooks and gather as much as data and information you can collect.
-UNKNOWN COMPILATION-
Well there is. There are, in fact, literally hundreds of ways to do this. I will discuss a few in this text to get you started. Every hacker has to start somehow and hacking web servers and ftp servers is one of the easiest ways.If you are reading this I am assuming that you already have a basic knowledge of how web servers work and how to use some form of UNIX. But I am going to
explain that stuff anyway for those of you who don't know.
Part 1: Simple UNIX Commands
Most DOS commands have UNIX and Linux equivalents. Listed below are
some of the main commands you will need to know to use a shell account.
HELP = HELPTo see who else is on the system you can type WHO. To get information about a specific user on the system type FINGER <username>. Using those basic UNIX commands you can learn all you need to know about the system you are using.
COPY = CP
MOVE = MV
DIR = LS
DEL = RM
CD = CD
Part 2: Cracking Passwords
On UNIX systems the file that contains the passwords for all the users on the system is located in the /etc directory. The filename is passwd. I bet your thinking....
"Great. All I have to do is get the file called /etc/passwd and I'll be a hacker."
If that is what you are thinking then you are dead wrong. All the accounts in the passwd file have encrypted passwords. Thesepasswords are one-way encrypted which means that there is no way to decrypt them. However, there are programs that can be used to obtain passwords from the file. The name of the program that I have found to be the best password cracker is called "Cracker Jack" This program uses a dictionary file composedof thousands of words. It compares the encrypted forms of the words in the list to the encrypted passwords in the passwd file and it notifies you when it finds a match.However you can use others like “Cain and Abel” or “John The Ripper (JTR)”
To get them,never forget that GOOGLE IS YOUR BEST FRIEND !!!Some wordlists can be found at the following ftp site: sable.ox.ac.uk/ pub/wordlists. To get to the wordlist that I usually use goto that ftp site then goto the American directory. Once you are there download the file called dic-0294.tar.Z which is about 4 MB. To use that file it must be uncompressed using a program like Gzip for DOS or Winzip for Windows. After uncompressing the file it should be a text file around 8 MB and it is best to put it in the same directory as your cracking program. To find out how to use Cracker Jack/John The Ripper just read the documentation that is included with it.
Part 3: The Hard Part (Finding Password Files)
Up till now I have been telling you the easy parts of hacking a
server. Now we get to the more difficult part. It's common sense. If the system administrator has a file that has passwords for everyone on his or her system they are not going to just give it to you. You have to have a way to retrieve the “/etc/passwd” file without logging into the system. There are 2 simple ways that this can sometimes be accomplished. Often the “/etc directory” is not blocked from FTP. To get the passwd file this way try using an FTP client to access the site anonymously then check the “/etc” directory to see if access to the passwd file is restricted. If it is not restricted then download the file and run Cracker Jack on it. If it is restricted then try plan B. On some systems there is a file called PHF in the “/cgi-bin” directory. If there is then you are in luck. PHF allows users to gain remote access to files (including the “/etc/passwd” file) over the world wide web. To try this method goto your web browser and type in this URL:
Then substitute the site you are trying to hack for the xxx.xxx.xxx.
http://xxx.xxx.xxx/cgi-bin/phf?Qalias=x%0a/bin/cat%20/etc/passwd
For example, if I wanted to hack St. Louis University (and I have already) Iwould type in
http://www.slu.edu/cgi-bin/phf?Qalias=x%0a/bin/cat%20/etc/passwdDon't bother trying www.slu.edu because I have already done it and told them about their security flaw.
Here's a hint: try www.spawn.com and www.garply.com
If the preceding to methods fail then try any way you can think of to get that file. If you do get the file and all the items in the second field are X or ! or * then the password file is shadowed. Shadowing is just a method of adding extra security to prevent hackers and other unwanted people from using the password file. Unfortunately there is no way to "unshadow" a password file
but sometimes there are backup password files that aren't shadowed. Try looking for files such as “/etc/shadow” and other stuff like that.
Part 4: Logging In To "Your" New Shell
OK....This is where you use what you found using Cracker Jack.
Usernames and passwords. Run your telnet client and telent to the server that you cracked the passwords for, such as www.slu.edu. When you are connected it will give a login screen that asks for a login names and password and usually information on the operating system that the server is using (usually UNIX,
linux, aix, irix, ultrix, bsd, or sometimes even DOS or Vax / Vms). Just type in the information you got after cracking the passwd file and whatever you know about UNIX to do whatever you feel like doing. But remember that
“Hacking isn't spreading viruses or causing damage to other computer systems. It is using your knowledge to increase your knowledge. “Part 5: Newbie Info
If you feel that you have what it takes to be a serious hacker then you must first know a clear definition of hacking and how to be an ethical hacker. Become familiar with Unix environments and if you are only just starting to learn to hack, visit a local library and find some books on various operating systems on the Internet and how they work. Or you could go to a book store and buy a couple Internet security books (They often explain how hackers penetrate systems and that is something a beginner could use as an advantage.),Join forums,read Ebooks and gather as much as data and information you can collect.
-UNKNOWN COMPILATION-